ISE 2023 (Regular) Solved Question Paper
Section - A
Answer any ten questions. (10x2=20)
a) Define cyber crime. Give an example.
Cybercrime is any illegal behavior, directed by means of electronic operations that targets the security of computers and data processed by them.
Examples:
(Cyber terrorists, Scammers, Malware attacks, Phishing attacks)
Cybercrime is a criminal activity that involves the use of electronic communication networks to commit illegal acts, there by harming individuals and organizations.
Examples:
(Committing fraud, trafficking in child pornography and intellectual property, stealing identities, or violating privacy)
b) What is spamming?
– Spamming is the use of electronic messaging systems like e-mails and other digital delivery systems and broadcast media to send unwanted bulk messages indiscriminately.
– The term spamming is also applied to other media like in internet forums, instant messaging, and mobile text messaging, social networking spam, junk fax transmissions, television advertising and sharing network spam.
c) What is cyber stalking? Give an example.
Cyberstalking is stalking that takes place using electronic devices or the internet. It is the technological harassment directed towards a specific individual.
Examples:
(Making rude, offensive, or suggestive online comments)
d) List the methods to prevent credit card frauds.
- Keep your credit card information secure.
- Update your passwords regularly.
- Don’t Use Unsecure Websites.
- Watch Out for Phishing Scams
- Use strong passwords and PINs.
- Don’t respond to phishing emails
- Be aware of scams.
e) What are key loggers? Mention the types.
– A keylogger, sometimes called a keystroke logger or keyboard capture.
– A keylogger is a type of spyware that monitors and records what you type on your computer or mobile phone. Keylogging software or hardware can be used to monitor activity for legal or illegal purposes.
Types:
- Software keyloggers.
- Hardware keyloggers.
f) Define phishing and smishing.
g) Define proxy server and anony mizer.
– A proxy server is another computer on the network which acts as an intermediary between your computer and other computers on the network.
– Anonymizer is an anonymous proxy which allows the user to browse Internet anonymously. When an attacker uses an anonymizer, the proxy removes all the identifying information to protect the privacy of the user.
h) How to minimize buffer overflow?
- Use a compiler that supports buffer overflow protection.
- Dynamic run-time checks.
- Disable stack execution.
- Use a firewall.
- Keep software up to date.
i) What is digital evidence? Give an example.
j) What is cyber forensics?
– Cyber Forensics is the scientific processes of identification
– Cyber forensics is the process of obtaining data as evidence for a crime (using electronic equipment) while adhering to correct investigative procedures to apprehend the offender by presenting the evidence to the court.
k) Define Cryptography.
Cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. The art of cryptography has been used to code messages for thousands of years and continues to be used in bank cards, computer passwords, and ecommerce.
Section - B
Answer any four of questions. (4x5=20)
1) What is elementary transpose cipher?
A Transposition Cipher is a cipher in which the plaintext message is rearranged by some means agreed upon by the sender and receiver. –In transposition ciphers, no new alphabet is created. The letters of the plaintext are just rearranged in some fashion.
Encryption process:
Divide the plaintext into blocks: Divide the plaintext message into blocks of equal size. If the message length is not divisible by the block size, pad the last block with extra characters, such as spaces or null characters.
Rearrange characters according to the key: Apply the transposition key to each block, rearranging the characters according to the specified pattern.
Combine rearranged blocks: Concatenate the rearranged blocks to form the ciphertext.
Decryption process:
Divide the ciphertext into blocks: Divide the ciphertext into blocks of the same size as the plaintext blocks.
Reverse the transposition: Apply the inverse of the transposition key to each block, rearranging the characters back to their original order.
Combine decrypted blocks: Concatenate the decrypted blocks to form the original plaintext message.
2. What is cyber law? Explain Indian IT Act 2000.
Cyber law is the part of the overall legal system that deals with the internet, cyberspace, and their respective legal issues. Cyber law covers a fairly broad area covering several subtopics including freedom of expression, access to and usage of the internet, and online privacy. Generically, cyber law is referred to as the Law of the Internet.
IT Act 2000:
- Section 65: This section deals with the offense of tampering with computer source documents.
- Section 66: This section deals with the offense of hacking into a computer system.
- Section 67: This section deals with the offense of publishing or transmitting obscene content in electronic form.
- Section 68: This section deals with the offense of dishonestly receiving stolen computer source code.
- Section 72: This section deals with the offense of disclosing password.
- Section 73: This section deals with the offense of making false electronic records.
3. What is social engineering? Explain its types.
Social Engineering is the malicious act of tricking a person into doing something by messing up his emotions and decision-making process.
Types:
Pretexting: Creating a false story or scenario to gain the victim’s trust and convince them to cooperate.
Phishing: Sending emails or text messages that appear to be from a legitimate source, such as a bank or social media platform, to trick the victim into revealing sensitive information.
Baiting: Leaving a tempting item, such as a USB drive or a link to a website, in a public place to entice the victim to pick it up or click on it, exposing their device or accessing their personal information.
Quid pro quo: Offering something of value in exchange for the victim’s cooperation, such as technical support or a prize, to trick them into revealing sensitive information or performing actions that compromise security.
Tailgating: Following someone into a secure area without proper authorization, exploiting their physical presence to gain unauthorized access.
4. Differentiate virus and worms.
| Virus | Worm |
| A computer virus is a program, where a code reproduces itself and then replicates itself to other programs. | A computer worm is an independent or free malicious program |
| The viruses need hosts to spread from one system or device to another. | Worms however do not need any host. |
| Its spreading speed is slower. | Its spreading speed is faster. |
| Viruses can’t be controlled by remote. | Worms can be controlled by remote. |
| It is more harmful. | It is less harmful as compared. |
| Viruses are executed via executable files. | Worms are executed via weaknesses in the system. |
| The virus spreads at a comparatively slower pace than a Worm. | A worm can quickly spread through a device and it can infect many devices or networks quickly. |
| The main purpose of the virus is to transform or modify the information. | The main aim of worms is to eat the system resources. |
| Some of the examples of computer viruses are; Creeper, Blaster, Slammer, etc. | Some of the examples of computer worms are Morris worm, storm worm, etc. |
| Antivirus software is employed for protection against viruses. | Worms can be identified and eliminated by the Antivirus and firewall. |
| The full form of the Virus is Vital Information Resources Under Siege. | Worms stand for Write-Once, Read-Many. |
| Viruses are executed through executable files/data. | Worms are executed through weaknesses in the system. |
5. Explain the digital Forensic life cycle.
Digital forensic investigation process involves several stages and steps to handle and manage the digital evidence that can be extracted from the crime scene
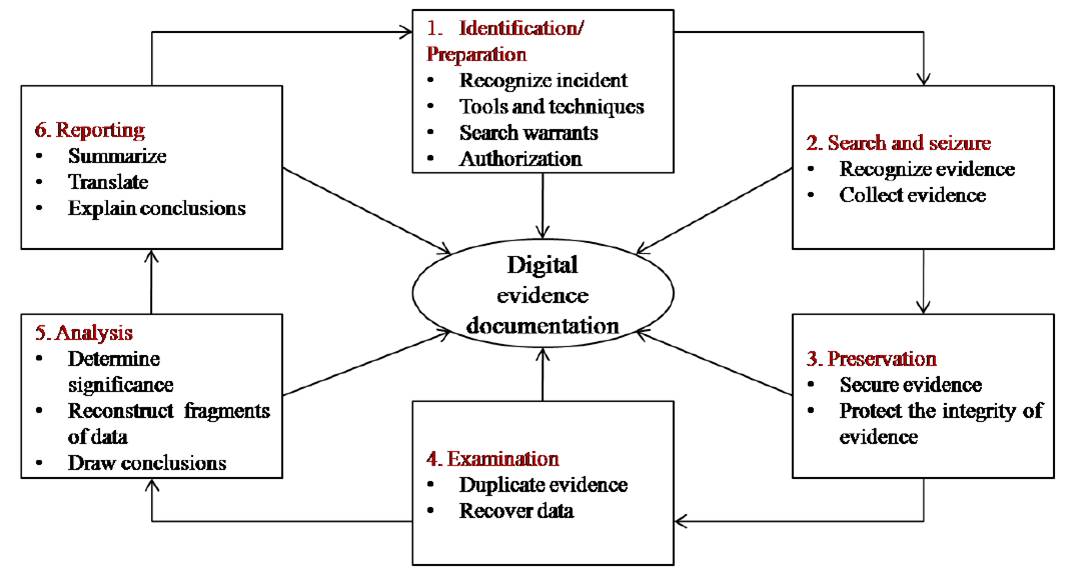
1. Preparing for the Evidence and Identifying the Evidence
In order to be processed and analysed, evidence must first be identified. It might be possible that the evidence may be overlooked and not identified at all. A sequence of events in a computer might include interactions between:
- Different files
- Files and file systems
2. Collecting and Recording Digital Evidence
Digital evidence can be collected from many sources. The obvious sources can be:
- Mobile phone
- Digital cameras
3. Storing and Transporting Digital Evidence
Care should be taken that evidence does not go anywhere without properly being traced. Things that can go wrong in storage include:
- Decay over time (natural or unnatural)
- Environmental changes (direct or indirect)
4. Examining/Investigating Digital Evidence
Forensics specialist should ensure that he/she has proper legal authority to seize, copy and examine the data. As a general rule, one should not examine digital information unless one has the legal authority to do so. Forensic investigation performed on data at rest (hard disk) is called dead analysis.
Some tools which can create entire hard drive images are:
- DCFLdd
- Iximager
- Guymager
5. Analysis, Interpretation and Attribution
In digital forensics, only a few sequences of events might produce evidence. But the possible number of sequences is very huge. The digital evidence must be analyzed to determine the type of information stored on it. Examples of forensics tools:
- Forensics Tool Kit (FTK)
- EnCase
- Scalpel (file carving tool)
- The Sleuth Kit (TSK)
6. Reporting
After the analysis is done, a report is generated. The report may be in oral form or in written form or both. The report contains all the details about the evidence in analysis, interpretation, and attribution steps. As a result of the findings in this phase, it should be possible to confirm or discard the allegations. Some of the general elements in the report are:
- Identity of the report agency
- Case identifier or submission number
- Case investigator
- Identity of the submitter
7. Testifying
This phase involves presentation and cross-examination of expert witnesses. An expert witness can testify in the form of:
- Testimony is based on sufficient facts or data
- Testimony is the product of reliable principles and methods
6. Write a note on Forensic auditing.
Benefits of a Forensic Audit?
- Uncovering of Corruption: In a Forensic Audit, while investigating fraud, an auditor would look out for the Conflicts of interest, Extortion, and Bribery.
- Uncovering of Asset Misappropriation, which reveals Misappropriation of cash, payments made to non-existing suppliers or employees, raising fake invoices, misuse of assets, or theft of Inventory, etc.
- Uncovering of Financial Statement Frauds which reveal intentional forgery of accounting records, non-disclosure of relevant details from the financial statements, omitting transactions – either revenue or expenses, or not applying the requisite financial reporting morals.
- It helps in Fraud Identification and Prevention, which generally occurs in financial transactions. It also helps in accounting and analyzing whether the company’s accounting policies are followed or not.
- It makes Sound Investment Decisions
- It assists in the formulation of Economic Policies.
- Forensic auditing is extremely rewarding as a career. It involves identifying, analysing, and reporting the findings during an audit and not only includes regular auditing and accounting activities.
- False and Wilful representation or Assertion
- Perpetrator of Representation
- Intention to deceive
- The representation must relate to a fact.
- The active concealment of facts
- Promise made with no intention of performing it;
- The representation must have deceived the other party.
- Any other act fitted to deceive
- Any such ‘act or omission’ that the law specially declares as void
- Wrongful Loss and Wrongful Gain is Immaterial
7. Explain DES algorithm.
Data Encryption Standard (DES) is a block cipher algorithm that takes plain text in blocks of 64 bits and converts them to ciphertext using keys of 48 bits. It is a symmetric key algorithm, which means that the same key is used for encrypting and decrypting data.
DES encryption process:
- Initial Permutation (IP): The data block is permuted using a fixed permutation table. This helps to randomize the data and make it more difficult to attack.
- Expansion: The data block is expanded from 64 bits to 48 bits. This is done by adding 32 zero bits to the end of the data block.
- Substitution: The expanded data block is passed through a substitution box (S-box) eight times. Each S-box is a table that maps 6-bit blocks of data to 4-bit blocks of data. The S-boxes are designed to provide a high degree of non-linearity in the encryption process.
- Permutation: The output of the S-boxes is permuted using a fixed permutation table. This helps to diffuse the data and make it more difficult to attack.
- Final Permutation (FP): The output of the last round is permuted using a fixed permutation table. This helps to restore the order of the bits in the data block.
- Round Key Mixing: The permuted data is combined with a subkey using the exclusive-or (XOR) operation. The subkey is generated from the original key using a key schedule algorithm.
- Repeat Steps 3-5: Steps 3-5 are repeated 15 more times, using different subkeys each time.
Section - C
Answer any four of questions. (4×10=40)
8. Explain different forms of cyber crime.
Cybercrime is criminal activity that either targets or uses a computer, a computer network or a networked device. Most cybercrime is committed by cybercriminals or hackers who want to make money. However, occasionally cybercrime aims to damage computers or networks for reasons other than profit. These could be political or personal.
Types:
1. Unauthorized Access and Hacking:
Unauthorized access means any kind of access without the permission of either of the rightful or person in charge of the computer, computer system or computer network. Hacking means an illegal intrusion into a computer system and/or network. Every act committed towards breaking into a computer and/or network is hacking. Hackers write or use ready-made computer programs to attack the target computer.
2. Web Hijacking:
Web hijacking means taking forceful control of another person’s website. In this case the owner of the website loses control over his website and its content.
3. Pornography:
Pornography means showing sexual acts in order to cause sexual excitement. The definition of pornography also includes pornographic websites, pornographic magazines produced using computer and the internet pornography delivered over mobile phones.
4. Child Pornography:
The Internet is being highly used as a medium to sexually abuse children. The children are viable victim to the cyber crime. Computers and internet having become a necessity of every household, the children have got an easy access to the internet. There is an easy access to the pornographic contents on the internet. Pedophiles lure the children by distributing pornographic material and then they try to meet them for sex or to take their nude photographs including their engagement in sexual positions. Sometimes Pedophiles contact children in the chat rooms posing as teenagers or a child of similar age and then they start becoming friendlier with them and win their confidence.
5. Cyber Stalking:
In general terms, stalking can be termed as the repeated acts of harassment targeting the victim such as following the victim, making harassing phone calls, killing the victims pet, vandalizing victims property, leaving written messages or objects. Stalking may be followed by serious violent acts such as physical harm to the victim. Cyber Stalking means repeated acts of harassment.
6. Denial of service Attack:
This is an attack in which the criminal floods the bandwidth of the victim’s network or fills his e-mail box with spam mail depriving him of the services he is entitled to access or provide. This kind of attack is designed to bring the network to crash by flooding it with useless traffic. Another variation to a typical denial of service attack is known as a Distributed Denial of Service (DDoS) attack
7. Virus attacks:
Viruses are the programs that have the capability to infect other programs and make copies of itself and spread into other program. Programs that multiply like viruses but spread from computer to computer are called as worms.
8. Software Piracy:
Software piracy refers to the illegal copying of genuine programs or the counterfeiting and distribution of products intended to pass for the original. These kind of crimes also include copyright infringement, trademarks violations, theft of computer source code, patent violations etc.
9. Salami attacks:
These attacks are used for the commission of financial crimes. The key here is to make the alteration so insignificant that in a single case it would go completely unnoticed. E.g. a bank employee inserts a program.
10. Phishing:
Phishing is the act of sending an e-mail to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
11. Internet time theft:
Internet time refers to usage by an unauthorized person of the Internet hours paid for by another person.
12. Theft of computer system:
This type of offence involves the theft of a computer, some part(s) of a computer or a peripheral attached to the computer.
9. (a & b)
a) What is a BOTNET? Explain the concept of bots used as frauds activities.
Botnets are networks of hijacked computer devices used to carry out various scams and cyberattacks. The term “botnet” is formed from the word’s “robot” and “network.” Assembly of a botnet is usually the infiltration stage of a multi-layer scheme. The bots serve as a tool to automate mass attacks, such as data theft, server crashing, and malware distribution.
Botnets use your devices to scam other people or cause disruptions
frauds activities:
Create fake accounts: Bots can be used to create fake accounts on social media platforms, e-commerce websites, and other online services. These fake accounts can then be used to spread misinformation, promote scams, or abuse the services.
Generate fake reviews: Bots can be used to generate fake reviews of products, services, and businesses. These fake reviews can be used to deceive consumers and manipulate search engine rankings.
Click on fraudulent ads: Bots can be used to click on fraudulent ads, generating fake traffic that can be used to defraud advertisers.
Steal data: Bots can be used to steal data from websites and databases, such as credit card numbers, passwords, and personal information. This data can then be used to commit identity theft, fraud, or other crimes.
Distribute malware: Bots can be used to distribute malware to other devices, such as through email attachments, drive-by downloads, or social engineering attacks. This malware can then be used to steal data, encrypt files for ransom, or take control of devices.
b) Explain different types of phishing techniques.
Phishing is a fraud technique where a malicious actor sends messages impersonating a legitimate individual or organization, usually via email or other messaging system. Many cyber attackers distribute malicious attachments and links through phishing emails to trick unsuspecting users into downloading malware.
Types:
1. Email Phishing
Email is the most popular phishing medium. Scammers register fake domains that impersonate real organizations and send thousands of requests to their targets.
2. Spear Phishing
Spear phishing works like common phishing attacks, using communications from a seemingly trusted source to trick victims. However, a spear phishing attack targets a specific individual or set of individuals rather than sending generic messages to many users in the hope that one falls for the trick. Popular targets include HR staff and IT managers because they have higher access levels within the wider organization.
3. Vishing and Smishing
Mobile phones replace email in smishing (SMS phishing) and vishing (voice phishing). With smishing, the attackers send text messages with similar deceptive content to a phishing email. Vishing involves phone conversations, with the scammer directly speaking to the target.
4. Clone Phishing
Although clone phishing attacks are not as sophisticated as spear phishing or whaling, they are still very effective. This attack method includes all major phishing tenants. The difference is that instead of impersonating an individual or organization to make a fraudulent request, the attacker copies legitimate emails previously sent by trusted entities.
5. Pharming
Pharming is a highly technical form of phishing, making it harder to detect. It involves a hacker hijacking the DNS (Domain Name Server), which converts URLs from plain language to IP addresses. When users enter the target website’s URL, the DNS redirects them to another IP address, usually of a malicious website that appears legitimate.
6. HTTPS Phishing
Hypertext Transfer Protocol Secure (HTTPS) uses encryption to enhance security, and most users consider it safe to click on HTTPS links. Most organizations today use HTTPS over standard HTTP to help establish the legitimacy of links. However, attackers can leverage HTTPS to make their links appear legitimate and increase the success of their phishing campaigns.
7. Pop-up Phishing
Most users install pop-up blockers, but pop-up phishing is still dangerous. Malicious actors may place malicious code in small notifications (pop-ups), which people see when they visit a website.
8. Evil Twin Phishing
Evil twin attacks often use fake WiFi hotspots that appear legitimate but can intercept sensitive data in transit. Malicious actors can eavesdrop or perform man-in-the-middle (MitM) attacks when someone uses a fake hotspot. Attackers can steal data sent over the connection, such as confidential information and login credentials.
10. Write note on followings
a) Network Forensic
Network forensics is a branch of digital forensics that focuses on the analysis of network traffic to identify and investigate cyberattacks. It is a critical tool for cybersecurity professionals, as it can be used to:
1. Investigate cyberattacks: Network forensics can be used to identify the source, methods, and scope of cyberattacks. This information can then be used to improve security measures and prevent future attacks.
2. Identify and resolve network performance issues: Network forensics can be used to identify and resolve network performance issues, such as bottlenecks and congestion. This can help to improve the overall performance and reliability of the network.
3. Enforce security policies: Network forensics can be used to monitor network traffic and ensure that it is compliant with company security policies. This can help to prevent unauthorized access to the network and data breaches.
4. Comply with regulations: Network forensics can be used to comply with regulations that require the monitoring and analysis of network traffic. This is especially important for organizations in industries such as healthcare and finance.
5. Support legal investigations: Network forensics can be used to support legal investigations by providing evidence of cybercrime. This can help to bring perpetrators to justice and recover stolen data.
b) Computer Forensic
Computer forensics, also called digital or cyber forensics, is a field of technology that uses investigation techniques to help identify, collect, and store evidence from an electronic device. Oftentimes computer forensics professionals uncover evidence that can be used by law enforcement agencies or by businesses and individuals to recover lost and damaged data. Read on to learn about the computer forensics types, techniques, career paths, and more.
Types of computer forensics
Computer forensics always involves gathering and analyzing evidence from digital sources. Some common types include:
1. Database forensics: Retrieval and analysis of data or metadata found in databases
2. Email forensics: Retrieval and analysis of messages, contacts, calendars, and other information on an email platform
3. Mobile forensics: Retrieval and analysis of data like messages, photos, videos, audio files, and contacts from mobile devices
4. Memory forensics: Retrieval and analysis of data stored on a computer’s RAM (random access memory) and/or cache
5. Network forensics: Use of tools to monitor network traffic like intrusion detection systems and firewalls
6. Malware forensics: Analysis of code to identify malicious programs like viruses, ransomware, or Trojan horses
11. (a & b)
a) Explain SQL injection techniques.
SQL Injection is a code-based vulnerability that allows an attacker to read and access sensitive data from the database. Attackers can bypass security measures of applications and use SQL queries to modify, add, update, or delete records in a database.
A successful SQL injection attack can badly affect websites or web applications using relational databases such as MySQL, Oracle, or SQL Server. In recent years, there have been many security breaches that resulted from SQL injection attacks.
Types of SQL Injection
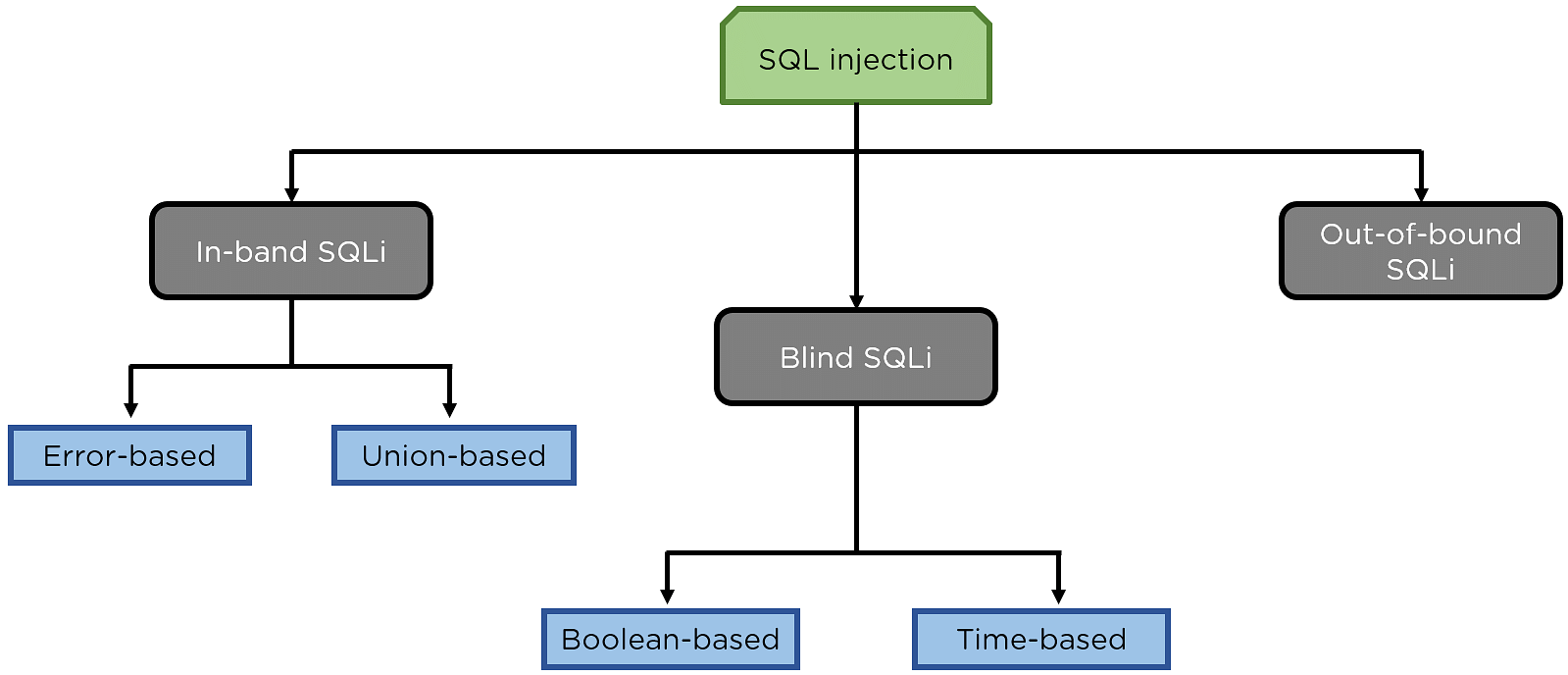
In-band SQLi – The attackers use the same communication channel to launch their attacks and collect results.
The two common types of in-band SQL injections are Error-based SQL injection and Union-based SQL injection.
- Error-based SQL injection – Here, the attacker performs certain actions that cause the database to generate error messages. Using the error message, you can identify what database it utilizes, the version of the server where the handlers are located, etc.
- Union-based SQL injection – Here, the UNION SQL operator is used in combining the results of two or more select statements generated by the database, to get a single HTTP response. You can craft your queries within the URL or combine multiple statements within the input fields and try to generate a response.
Blind SQLi – Here, it does not transfer the data via the web application. The attacker can not see the result of an attack in-band.
- Boolean-based SQL Injection – Here, the attacker will send an SQL query to the database asking the application to return a different result depending on whether the query returns True or False.
- Time-based SQL Injection – In this attack, the attacker sends an SQL query to the database, which makes the database wait for a particular amount of time before sharing the result. The response time helps the attacker to decide whether a query is True or False.
Out-of-bound SQL Injection – Out-of-bound is not so popular, as it depends on the features that are enabled on the database server being used by the web applications. It can be like a misconfiguration error by the database administrator.
b) Explain Attacks on wireless networks.
Wireless networks are susceptible to a variety of attacks, which can be broadly categorized into three types: passive attacks, active attacks, and denial-of-service attacks.
Types of Wireless Network Attacks
Wireless networks have undoubtedly revolutionized the way we communicate and conduct business, offering unparalleled convenience and mobility. However, with this freedom comes the lurking threat of malicious attackers seeking to exploit the vulnerabilities inherent in wireless technology. Here are some of the common types of wireless network attacks:
1. Wireless Eavesdropping (Passive Attacks)
Attackers use tools like packet sniffers to intercept and monitor wireless communications between devices. By capturing data packets transmitted over the air, they can potentially obtain sensitive information, such as login credentials, financial data, or personal information.
2. Wireless Spoofing (Man-in-the-Middle Attacks)
In these attacks, the attacker positions themselves between the wireless client and the legitimate access point, intercepting and manipulating data transmissions. The attacker may then relay the information back and forth, making it appear as if they are the legitimate access point. This enables them to snoop on data or perform other malicious actions unnoticed.
3. Wireless Jamming (Denial-of-Service Attacks)
Attackers flood the wireless frequency spectrum with interference signals, disrupting legitimate communications between devices and access points. By creating excessive noise, they can render the wireless network unusable for legitimate users.
4. Rogue Access Points
Attackers set up unauthorized access points, mimicking legitimate ones, to deceive users into connecting to them. Once connected, the attacker can eavesdrop, capture data, or launch further attacks on the unsuspecting users.
5. Brute-Force Attacks
Attackers try various combinations of passwords or encryption keys in rapid succession until they find the correct one to gain unauthorized access to the wireless network.
6. WEP/WPA Cracking
Attackers exploit vulnerabilities in older wireless security protocols like Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA) to gain unauthorized access to encrypted wireless networks.
7. Evil Twin Attacks
Attackers create fake access points with names similar to legitimate ones, tricking users into connecting to the malicious network. Once connected, the attacker can intercept sensitive data or execute further attacks.
8. Deauthentication/Disassociation Attacks
Attackers send forged deauthentication or disassociation frames to wireless devices, forcing them to disconnect from the network, leading to service disruptions or potential vulnerabilities when devices automatically reconnect.
12. Explain Chinese remainder theorem with an example.
The Chinese remainder theorem (CRT) is a theorem in number theory that provides a way to solve a system of simultaneous congruences. It states that if the moduli in the congruences are pairwise coprime, then there exists a unique solution modulo the product of the moduli.
In simpler terms, the CRT allows us to find a number that satisfies a set of conditions, where each condition specifies the remainder when the number is divided by a different integer. The moduli must be pairwise coprime, meaning they have no common factors other than 1.
Consider the following example:
Find an integer x such that:
x ≡ 2 (mod 3)
x ≡ 3 (mod 5)
x ≡ 2 (mod 7)
Since the moduli 3, 5, and 7 are pairwise coprime, we can apply the CRT to solve this system of congruences.
First, we calculate the Chinese remainder theorem coefficients:
M1 = (5 * 7) / 3 = 35
M2 = (3 * 7) / 5 = 42
M3 = (3 * 5) / 7 = 21
Next, we calculate the residues:
R1 = 35 * 2 / 3 = 23
R2 = 42 * 3 / 5 = 25
R3 = 21 * 2 / 7 = 6
Finally, we calculate the solution:
x ≡ 23 * 1^(-1) (mod 35) + 25 * 2^(-1) (mod 35) + 6 * 3^(-1) (mod 35)
x ≡ 23 – 50 + 18 (mod 35)
x ≡ -9 (mod 35)
Therefore, the unique solution modulo the product of the moduli is x ≡ 26 (mod 105).
