Cyber Security & Cyber Law
5 Marks (IMP)
1. Write any five different definitions of cyber crime?
a) Cybercrime refers to criminal activities that are carried out using computers, networks, or digital devices as the primary means of perpetration. These activities include hacking, malware distribution, identity theft, financial fraud, and other illicit actions that exploit vulnerabilities in digital systems for unlawful purposes.
b) Cybercrime encompasses illegal activities that are facilitated by or targeted at computer networks, systems, or online platforms. This includes offenses such as unauthorized access to computer systems, denial-of-service attacks, phishing scams, and the dissemination of malicious software for nefarious purposes.
c) Cybercrime involves unlawful acts that leverage technology and the internet, encompassing a wide range of offenses such as online harassment, cyberbullying, data breaches, and the theft of intellectual property through digital means.
d) Cybercrime refers to criminal activities that exploit weaknesses in information technology systems and networks, leading to financial fraud, data theft, online extortion, and the disruption of critical infrastructure through the use of malicious software or unauthorized access.
e) Cybercrime encompasses a broad spectrum of illegal activities committed in cyberspace, including but not limited to identity theft, online scams, cyber espionage, and the dissemination of illicit content or materials through digital channels.
2. Explain the various categories of cyber criminals?
Cyber criminals can be categorized into several distinct groups based on their objectives, expertise, and the nature of their illegal activities:
1. Hackers: These individuals possess advanced technical skills and knowledge of computer systems. They aim to gain unauthorized access to networks, systems, or databases, often for the purpose of data theft, system disruption, or espionage.
2. Malware Developers: Cyber criminals in this category specialize in creating malicious software, such as viruses, worms, trojans, and ransomware, designed to infiltrate systems, corrupt data, or extort money from victims.
3. Phishers: Phishers are adept at crafting deceptive communications, such as emails or websites, that appear legitimate to trick individuals into divulging sensitive information, such as login credentials, financial details, or personal data.
4. Scammers and Fraudsters: These individuals use various online schemes to deceive and defraud individuals or organizations for financial gain. This can include investment scams, romance scams, and fraudulent schemes targeting unsuspecting victims.
5. State-Sponsored Actors: Some cyber criminals operate with the support or approval of nation-states, engaging in cyber espionage, sabotage, or the theft of intellectual property to advance national interests.
6. Cyber Extortionists: These individuals employ tactics such as ransomware attacks and distributed denial-of-service (DDoS) threats to extort money from individuals or organizations by disrupting or threatening to disrupt their operations.
3. Explain the following
a) credit card fraud
Credit card fraud occurs when unauthorized individuals use stolen or counterfeit credit card information to make fraudulent purchases or transactions. This illegal activity can take various forms, including:
1. Card Theft: Criminals may physically steal credit cards or intercept them during transit to obtain card details for unauthorized use.
2. Skimming: This involves the use of a small, covert device to capture credit card information during legitimate transactions. The stolen data is then used to create counterfeit cards or for online purchases.
3. Card-Not-Present Transactions: Fraudulent purchases can be made online or over the phone using stolen credit card details without the physical presence of the card.
4. Account Takeover: Cybercriminals gain unauthorized access to a victim’s credit card account through phishing scams, malware, or social engineering, allowing them to make unauthorized transactions.
5. Identity Theft: Fraudsters use stolen personal information, including credit card details, to open new accounts or make unauthorized transactions under a victim’s identity.
To mitigate the risks of credit card fraud, individuals and businesses should stay vigilant against phishing attempts, regularly monitor their card statements for unauthorized transactions, securely store their cards, and promptly report any suspected fraudulent activity to their card issuer. Additionally, using secure payment methods and implementing strong authentication measures can help reduce the likelihood of falling victim to credit card fraud.
b) Internet time theft
Internet time theft, also known as cyberslacking or time theft, refers to the unauthorized use of an employer’s internet resources and time for non-work-related activities during working hours. This can encompass various behaviors, such as excessive personal web browsing, social media usage, online shopping, or engaging in activities unrelated to work responsibilities.
Internet time theft can impact work productivity, use up network resources, and potentially compromise network security. To address this issue, employers often implement policies and tools to monitor and restrict non-work-related internet usage during working hours. Clear communication of acceptable internet usage at work, along with appropriate enforcement of policies, can help mitigate internet time theft and promote a more productive work environment.
7 Types of Time Theft
Time theft is a challenging issue for employers because there are so many ways it can occur, from the fairly innocuous extra five minutes in the example above to cases of fraud perpetrated via falsified timesheets or records. The list below explores some of the more common types of time theft that employers might encounter.
1. Extended or excessive breaks
Whether it’s a lunch break that extends beyond the time permitted or an excessive number of short breaks (with smoke breaks being a typical culprit), this type of time theft is not only common but can also be difficult to detect.
2. Inflation of work hours
This form of time theft involves anything that results in inflated work hours being reported and compensated. While an employee might do it unintentionally (or under a mistaken belief that it helps out the payroll department, as in the example above), inflation of work hours also includes timesheet falsification and time clock manipulation.
3. Personal, nonwork-related activities
Tackling a personal matter during work hours can be unavoidable sometimes, but when employees do this frequently or consistently—for example, answering personal calls, checking personal emails or working on a side hustle—those lost minutes add up over time.
4. Digital distractions and cyberslacking
Social media and web surfing are digital distractions that come with a double whammy: Not only does the time spent online for nonwork-related matters add up, it can also result in reduced focus on the work that needs to be done and an overall decline in both productivity and work quality.
5. Buddy punching
It turns out there’s a specific term to describe the practice of asking a coworker to cover for their late arrival or early departure by clocking in or out for them: buddy punching. Buddy punching can happen with both manual and electronic timekeeping procedures. For example, many electronic timekeeping processes assign users with PINs for signing in or out, which an employee can easily give to a coworker to clock in or out for them.
6. Late arrivals/early departures
As illustrated by the numbers in the example in the previous section, arriving a little late for work or leaving work early might look insignificant, but over time a consistent pattern of late arrivals or early departures can add up—especially if you have multiple employees engaging in this practice.
7. Intentional time wasting
This type of time theft covers a wide range of employee behavior, from taking too long to complete a project (sometimes resulting in otherwise unnecessary overtime) to padding the time worked on a task to stopping work early but waiting to clock out at the correct time.
c) Intellectual property crime?
Intellectual property (IP) crime involves the unauthorized use, reproduction, or distribution of protected works and assets, such as inventions, creative works, and trademarks. This encompasses several forms of illegal activities:
- Copyright Infringement: This occurs when someone reproduces, distributes, or displays copyrighted works (such as literature, music, or software) without the permission of the copyright holder.
- Trademark Counterfeiting: Criminals produce and sell goods bearing fake trademarks, often imitating well-known brands, to deceive consumers and profit from the reputation of legitimate products.
- Patent Infringement: Unauthorized use, manufacture, or sale of patented technologies or inventions without the permission of the patent holder constitutes patent infringement.
- Trade Secret Theft: This involves the unauthorized acquisition, use, or disclosure of proprietary information, such as formulas, processes, or customer lists, that provide a business with a competitive advantage.
- Piracy: This includes the unauthorized reproduction and distribution of digital media, such as movies, music, and software, often perpetuated through online channels.
Intellectual property crime poses significant economic and reputational threats to creators, innovators, and businesses. Law enforcement agencies, along with regulatory bodies, employ various measures to detect, investigate, and prosecute IP crimes, while businesses implement strategies to protect their intellectual assets through legal recourse, digital rights management, and cybersecurity measures.
4. Explain about legal perspectives of Cybercrimes?
From a legal perspective, cybercrimes are addressed through a combination of national and international laws, regulations, and enforcement mechanisms. Several key legal perspectives of cybercrimes include:
- Jurisdiction: Determining the jurisdiction and applicable laws for cybercrimes can be complex, especially when offenders and victims are in different countries. International cooperation and mutual legal assistance treaties are essential for addressing cross-border cybercrimes effectively.
- Legislation and Regulation: Many countries have enacted specific cybercrime laws to criminalize unauthorized access to computer systems, data interference, electronic fraud, and other illicit activities involving information technology. In addition, regulations and directives often address data protection, privacy rights, and cybersecurity standards.
- Law Enforcement and Investigation: Law enforcement agencies are responsible for investigating cybercrimes, collecting electronic evidence, and identifying perpetrators. Specialized cybercrime units and digital forensics capabilities are essential for addressing the unique challenges of investigating crimes in cyberspace.
- Prosecution and Legal Remedies: Prosecuting cybercriminals involves presenting electronic evidence in court and applying relevant laws to secure convictions. Legal remedies for cybercrimes can include fines, imprisonment, asset forfeiture, and restitution to victims.
- International Cooperation: Given the transnational nature of many cybercrimes, international cooperation among law enforcement agencies and judicial authorities is crucial for effective investigation, prosecution, and extradition of cybercriminals.
- Victim Support and Data Privacy: Legal frameworks often include provisions for protecting the rights of cybercrime victims, including support services and mechanisms for reporting and addressing incidents. Data privacy laws also play a critical role in regulating the collection, use, and protection of personal information in the context of cybercrimes.
These legal perspectives are essential for ensuring that cybercrimes are effectively addressed, perpetrators are held accountable, and victims are provided with the necessary support and protection under the law.
5. Explain about Indian perspectives of Cybercrimes?
In India, the legal framework for addressing cybercrimes is still evolving. However, there have been several significant developments in recent years. Here are some key Indian perspectives of cybercrimes:
- Information Technology Act, 2000: The Information Technology Act, 2000, is the primary legislation governing cybercrimes in India. The Act defines various cybercrimes, such as hacking, cyberstalking, and identity theft, and provides for penalties for these offenses. The Act also includes provisions for the admission of electronic evidence in court and the establishment of adjudicating authorities for the speedy resolution of disputes related to cybercrimes.
- Cybercrime Investigation Cell: The Cybercrime Investigation Cell (CBI-CIC) is a specialized unit within the Central Bureau of Investigation (CBI) responsible for investigating cybercrimes in India. The CBI-CIC works closely with other law enforcement agencies, both in India and abroad, to investigate and prosecute cybercrimes.
- National Cybercrime Policy: The National Cybercrime Policy was released in 2013 to provide a comprehensive framework for addressing cybercrimes in India. The policy aims to enhance the capabilities of law enforcement agencies to investigate and prosecute cybercrimes, promote cybercrime awareness, and strengthen international cooperation in the fight against cybercrime.
- Section 67C of the IT Act: Section 67C of the IT Act requires intermediaries, such as internet service providers and social media companies, to retain certain information about their users for a period of 180 days. This information includes the user’s name, IP address, email address, and other details. The provision has raised concerns about user privacy and the potential for misuse of this information by law enforcement agencies.
- Cybercrime and Fake News: In recent years, there has been a significant increase in the number of cybercrimes related to fake news and propaganda. The Indian government has taken several measures to address this issue, including the establishment of a fact-checking unit within the Press Information Bureau and the introduction of new regulations for social media companies.
- Aadhaar data breaches: Aadhaar is a biometric-based identity system in India that has been the target of several cyberattacks and data breaches. The government has taken several measures to strengthen the security of the Aadhaar system, including the introduction of new regulations and the establishment of a dedicated agency to oversee the system’s security.
The Indian legal framework for addressing cybercrimes is still evolving, but there have been several significant developments in recent years. The Information Technology Act, 2000, provides a legal framework for addressing cybercrimes, and the Cybercrime Investigation Cell and the National Cybercrime Policy provide a comprehensive framework for investigating and preventing cybercrimes. However, concerns about user privacy and the potential for misuse of user data by law enforcement agencies remain. The Indian government has also taken several measures to address the issue of fake news and propaganda and strengthen the security of the Aadhaar system.
6. Explain the following
a) E-Mail Virus attack/dissemination of viruses
An email virus attack refers to the distribution of malicious software, often in the form of attachments or links within emails, with the intention of infecting the recipient’s computer or network. Several methods are commonly employed to disseminate viruses via email, including:
- Infected Attachments: Cybercriminals may send emails with attachments containing malware, such as viruses, trojans, or ransomware. These attachments are often disguised as legitimate files, such as documents, PDFs, or executable programs.
- Phishing Links: Emails may contain links to fake websites designed to trick recipients into entering sensitive information, which can lead to malware being downloaded onto the recipient’s device.
To mitigate the risk of email virus attacks, individuals and organizations can implement the following best practices:
- Use Antivirus and Antimalware Software: Deploy robust antivirus and antimalware solutions that can detect and quarantine malicious attachments or links within emails.
- Employee Training: Conduct cybersecurity awareness training to educate employees about recognizing suspicious emails, avoiding clicking on unknown links, and refraining from downloading attachments from unverified sources.
- Email Filtering and Security: Implement email filtering and security solutions to automatically detect and block malicious emails before they reach users’ inboxes.
- Regular Software Updates: Keep all software, including email clients and operating systems, up to date with the latest security patches to prevent vulnerabilities that can be exploited by email-borne viruses.
- Verify Sender Identities: Encourage individuals to verify the authenticity of email senders, especially when receiving unexpected attachments or requests for sensitive information.
By incorporating these measures, individuals and organizations can enhance their defenses against email virus attacks and reduce the risk of infection and potential data breaches.
b) E-Mail bombing/mail bombs
Email bombing, also known as mail bombing, involves sending a massive volume of emails to a specific email address or domain with the intention of overwhelming the recipient’s inbox and disrupting their email communication. This type of attack can cause significant inconvenience, as it may render the recipient’s email account unusable due to the sheer volume of incoming messages.
Email bombing attacks can lead to various adverse effects, including:
- Denial of Service: The overwhelming volume of incoming emails can result in a denial of service, making it difficult or impossible for the recipient to access or use their email account.
- Resource Consumption: Email servers and infrastructure may become strained or overwhelmed due to the excessive volume of incoming messages, impacting overall email service availability.
- Disruption of Communication: Email bombing can disrupt an individual’s or organization’s ability to send, receive, and manage legitimate emails, causing communication breakdowns.
To mitigate the effects of email bombing, individuals and organizations can consider implementing the following measures:
- Email Filtering: Employ email filtering solutions that can identify and block large volumes of unsolicited emails from reaching the recipient’s inbox.
- Rate Limiting: Email servers can be configured to impose rate limits on incoming messages from specific sources, thereby preventing an overwhelming influx of emails.
- Security Awareness: Educate email users about recognizing and reporting suspicious email activity, which can help in identifying email bombing attacks early.
- Network Monitoring: Implement network monitoring tools and intrusion detection systems to detect and respond to abnormal email traffic patterns indicative of email bombing activity.
By adopting these preventive strategies, individuals and organizations can better protect themselves against the disruptive effects of email bombing attacks and maintain the integrity of their email communication. Additionally, promptly reporting instances of email bombing to internet service providers or relevant authorities can aid in addressing and mitigating such attacks.
c) Logic bomb
A logic bomb is a type of malicious code that is intentionally inserted into a software system or network with the purpose of lying dormant until certain conditions are met, at which point it is triggered to execute a harmful action. These harmful actions can range from deleting files, corrupting data, or causing system malfunctions to initiating a denial-of-service attack, depending on the design and intent of the logic bomb.
Key characteristics of logic bombs include:
- Triggering Event: Logic bombs are programmed to activate based on specific conditions, such as reaching a particular date or time, the occurrence of a specific system event, or the execution of a particular program.
- Concealment: They are often disguised within legitimate software or systems, making them challenging to detect until they are triggered.
- Intent: Their primary purpose is to cause damage, disrupt systems, or facilitate unauthorized access to data or resources.
To mitigate the risk of logic bomb attacks, organizations and individuals can consider implementing the following measures:
- Code Review: Thoroughly review and validate all code, scripts, and applications to identify any suspicious or undocumented elements that may indicate the presence of a logic bomb.
- Access Control: Enforce strict access controls to prevent unauthorized individuals from inserting malicious code into critical systems or applications.
- System Monitoring: Implement robust system monitoring and anomaly detection mechanisms to identify unusual activities or unauthorized changes that may signal the presence of a logic bomb.
- Security Awareness: Educate employees and users about the risks associated with insider threats and the potential presence of logic bombs, encouraging the reporting of any suspicious or unexpected system behavior.
By incorporating these preventive strategies and maintaining a proactive stance towards insider threats, organizations and individuals can improve their resilience against potential logic bomb attacks and reduce the associated risks to their systems and data.
d) Trojan Horse
A Trojan Horse, or simply Trojan, is a type of malicious software that masquerades as a legitimate file or program to deceive users into executing it. Once activated, a Trojan can perform various harmful actions, such as stealing sensitive information, corrupting files, installing additional malware, or providing unauthorized access to the compromised system. Unlike viruses and worms, Trojans do not replicate themselves but rely on social engineering tactics to infiltrate and deceive users.
Trojans can be distributed through various means, including malicious email attachments, fake software downloads, or compromised websites.
Common types of Trojans include:
- Backdoor Trojans: These Trojans create a “backdoor” entry point into the infected system, allowing attackers to gain unauthorized access and control over the compromised system.
- Remote Access Trojans (RATs): RATs enable attackers to remotely control the infected system, potentially leading to the theft of sensitive information or the manipulation of the compromised device.
- Banking Trojans: These Trojans are designed to steal financial information, login credentials, and other sensitive data related to online banking and financial transactions.
To mitigate the risks posed by Trojan attacks, individuals and organizations can implement the following best practices:
- Use Antivirus and Antimalware Software: Deploy robust antivirus and antimalware solutions that can detect and remove Trojan infections.
- Exercise Caution with Email Attachments and Downloads: Verify the authenticity of email attachments and avoid downloading software from untrusted sources to minimize the risk of Trojan infections.
- Keep Software Updated: Regularly update operating systems, applications, and security software to patch known vulnerabilities that could be exploited by Trojans.
- User Awareness Training: Educate users about the risks of downloading and executing unknown files and the importance of exercising caution when browsing the internet and accessing emails.
By implementing these measures and maintaining a proactive stance against malware threats, individuals and organizations can strengthen their defenses against Trojan attacks and reduce the likelihood of compromise.
e) Software piracy
Software piracy refers to the unauthorized copying, distribution, or use of copyrighted software, in violation of the software license agreements and intellectual property laws. This illegal practice encompasses various activities, including:
- End-User Piracy: Involves individuals or organizations using unauthorized copies of software, often beyond the scope of the purchased license.
- Counterfeiting: Infringing parties reproduce and distribute counterfeit copies of software, often replicating the packaging and branding to deceive consumers.
- Online Piracy: Unlawful sharing of software over the internet through file-sharing platforms, torrent sites, or other unauthorized distribution channels.
Software piracy poses several detrimental effects, including financial losses for software developers, diminished incentives for innovation, potential security risks from unpatched software, and the proliferation of unlicensed, potentially vulnerable software across businesses and individuals.
To combat software piracy, software developers, industry organizations, and law enforcement agencies employ various approaches, such as:
- Licensing and Activation: Implementing robust licensing mechanisms and activation procedures to control access to software and deter unauthorized usage.
- Anti-Piracy Measures: Introducing technological measures, such as digital rights management (DRM) and software protection mechanisms, to safeguard against unauthorized duplication and use.
- Legal Enforcement: Pursuing legal action against individuals, organizations, or entities engaged in software piracy to uphold intellectual property rights and enforce copyright laws.
- Education and Awareness: Raising awareness among consumers and businesses about the ethical, legal, and security implications of using pirated software, and educating about the benefits of genuine software acquisition.
By adopting these proactive strategies and collaborative efforts, the software industry strives to mitigate the prevalence of software piracy, protect intellectual property rights, and promote a legal and ethical software acquisition and distribution ecosystem.
7. Explain the classification of cyber crime?(5 Marks OR 10 Marks)
Cybercrimes can be classified into various categories based on the nature of the illegal activities and the objectives of the perpetrators. Some common classifications of cybercrimes include:
- Financial Cybercrimes: These include online fraud, financial manipulation, identity theft, credit card fraud, and illicit financial transactions carried out through online platforms or digital channels.
- Cyber Theft: Cyber theft encompasses the unauthorized acquisition of sensitive data, intellectual property, or financial assets, often through hacking, unauthorized access, or phishing schemes.
- Cyber Espionage: State-sponsored or corporate espionage activities involve the unauthorized acquisition of confidential or proprietary information for political, economic, or competitive advantage.
- Cyber Terrorism: Cyber terrorism involves the use of digital tools and technologies to disrupt critical infrastructure, cause widespread fear, or coerce government or civilian populations for ideological, religious, or political motives.
- Online Harassment and Stalking: This category includes cyberbullying, online harassment, cyberstalking, and other forms of digital abuse and intimidation.
- Malicious Software (Malware) Distribution: This involves the creation, distribution, and deployment of malware, including viruses, worms, trojans, ransomware, and other malicious applications designed to compromise systems and data.
- Denial of Service (DoS) Attacks: Perpetrators initiate DoS attacks to disrupt access to online services, websites, or networks by flooding them with an overwhelming volume of traffic, rendering them inaccessible to legitimate users.
- Child Exploitation and Abuse: This category involves the use of digital platforms to produce, distribute, or access child pornography, or to engage in predatory behavior towards minors.
Understanding these classifications is crucial for developing effective cybersecurity measures, law enforcement strategies, and legal frameworks to combat cybercrime and protect individuals, businesses, and critical digital infrastructure from malicious activities.
8. Discuss about the Indian ITA 2000? (5 Marks OR 10 Marks)
Sure! The Information Technology Act, 2000 (ITA 2000) is the primary legislation governing cybercrime and electronic commerce in India. Here are some key provisions of the Act:
- Definition of Cybercrime: The ITA 2000 defines various cybercrimes, such as hacking, cyberstalking, and identity theft, and provides for penalties for these offenses.
- Admission of Electronic Evidence: The ITA 2000 provides for the admissibility of electronic evidence in court, which is a critical provision for prosecuting cybercrimes.
- Adjudicating Authorities: The ITA 2000 establishes adjudicating authorities for the speedy resolution of disputes related to cybercrimes, cyber activities, and electronic commerce.
- Intermediary Liability: The ITA 2000 provides safe harbor provisions for intermediaries, such as internet service providers and social media companies, under which they are not liable for third-party content transmitted, stored, or hosted on their platforms. However, intermediaries must remove or disable access to any unlawful content upon receiving actual knowledge or on being notified by the appropriate government or its agency.
- Digital Signatures: The ITA 2000 recognizes digital signatures as a valid and legal method of signing electronic documents and provides for the establishment of a certification authority to issue and manage digital certificates.
- Cyber Appellate Tribunal: The ITA 2000 established the Cyber Appellate Tribunal (CAT) to hear appeals against orders passed by adjudicating authorities and to provide a forum for the speedy resolution of disputes related to cybercrime, cyber activities, and electronic commerce.
- Amendments to the ITA 2000: The ITA 2000 has been amended several times to strengthen the legal framework for addressing cybercrime and electronic commerce in India. In 2008, the Act was amended to include provisions for the punishment of cyberterrorism, and in 2018, the Act was further amended to include provisions for the punishment of the publication or transmission of material depicting children in sexually explicit acts.
In summary, the ITA 2000 provides a legal framework for addressing cybercrime and electronic commerce in India. The Act defines various cybercrimes, provides for the admissibility of electronic evidence, establishes adjudicating authorities and a Cyber Appellate Tribunal, and sets out provisions for intermediary liability and digital signatures. The Act has been amended several times to strengthen the legal framework for addressing cybercrime and electronic commerce in India.
9. Explain the 3 phases involved in planning cybercrime?
Reconnaissance: This phase involves gathering information about the target, including identifying potential vulnerabilities, strengths, and weaknesses in the target’s systems or individuals. This phase may involve passive activities such as monitoring social media, websites, and other publicly available information, as well as more active techniques such as scanning for network vulnerabilities or conducting phishing campaigns to gather user credentials.
Weaponization: In this phase, the cybercriminal develops or acquires the tools and resources necessary to execute the cyber attack. This may involve developing malware, acquiring exploit kits, or purchasing access to botnets or other resources that can be used to carry out the attack.
Delivery and Exploitation: This phase involves the actual execution of the cyber attack. This can include delivering malware to the target’s systems, exploiting vulnerabilities to gain unauthorized access, or carrying out social engineering attacks to manipulate individuals into divulging sensitive information or performing actions that benefit the cybercriminal.
10. What is social engineering? Explain the types of social engineers or classification of social engineering?
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. It is a common tactic used by cybercriminals to gain unauthorized access to systems, obtain sensitive information, or manipulate individuals for their own benefit.
There are various types of social engineers or classifications of social engineering. Some common types include:
- Phishing: This involves sending deceptive emails or messages that appear to be from a legitimate source, such as a bank or a trusted organization, in order to trick recipients into revealing sensitive information, such as passwords or credit card numbers.
- Pretexting: In this type of social engineering, the attacker creates a fabricated scenario or pretext to engage the target in a way that increases the likelihood that the target will divulge information or perform actions that they otherwise would not.
- Baiting: Baiting involves the promise of a good that induces a person to do a particular action. An example of this is a cybercriminal leaving a USB drive in a conspicuous location, such as a parking lot, in the hopes that someone will pick it up, insert it into a computer, and unknowingly install malware.
- Quid pro quo: In this type of social engineering, an attacker offers a benefit or a service in exchange for information or access. For example, an attacker may pose as a technical support representative and offer to help with a computer problem in exchange for remote access to the victim’s system.
11. What is cyber stalking? Explain its types?
Cyberstalking refers to the persistent and unwanted surveillance, harassment, or intimidation of an individual or group through electronic communication, such as the internet, social media, email, or other forms of digital communication. It often involves a pattern of behavior that instills fear, distress, or discomfort in the victim.
There are several types of cyberstalking, including:
- Email Stalking: The stalker repeatedly sends threatening or harassing emails to the victim. This may include explicit threats or disturbing content designed to intimidate or frighten the victim.
- Social Media Stalking: The stalker uses social media platforms to monitor the victim’s online activities, often commenting on or sharing the victim’s posts in a manner that is intended to intimidate or harass.
- Online Identity Theft: The stalker may impersonate the victim online, creating fake social media accounts or posting false information in the victim’s name in an attempt to damage their reputation or provoke fear.
- Doxing: This involves researching and publishing private or identifying information about the victim online, such as their home address, phone number, or other personal details, with the intent to intimidate or harass.
- GPS Tracking: In some cases, cyberstalks may use technology to track the victim’s physical location, such as by hacking into their mobile device or using GPS tracking devices without their knowledge or consent.
Cyberstalking can have serious emotional, psychological, and even physical consequences for the victim. It is important for individuals who believe they are being cyberstalked to document and report the behavior to law enforcement and seek support from trusted individuals or organizations.
12. What are the security tips for cyber cafe?
Security in a cyber cafe is crucial to protect both the business and its customers.
Here are some essential security tips for cyber cafes:
1. Secure Network: Ensure that the cyber cafe’s Wi-Fi network is secure with strong encryption, unique and complex passwords, and regular monitoring for unauthorized access.
2. Updated Software: Keep all computers and devices in the cyber cafe up to date with the latest operating system updates, antivirus software, and security patches to protect against known vulnerabilities.
3. User Access Controls: Implement strong password policies for user accounts and use individual accounts for each customer to prevent unauthorized access and improve accountability.
4. Privacy Screens: Install privacy screens or position computer monitors in a way that prevents unauthorized viewing of customers’ screens to protect their privacy.
5. Data Encryption: Utilize encryption for sensitive customer data, such as login credentials or payment information, to prevent unauthorized access in the event of a security breach.
6. Secure Payment Processing: If the cyber cafe offers payment services, ensure that the payment processing systems adhere to industry standards for security and compliance, such as PCI DSS.
7. Clear Policies: Establish and communicate clear usage policies to customers, including guidelines for secure behavior, prohibited activities, and the consequences of violating the policies.
8. Regular Backups: Implement regular data backups to prevent data loss in the event of a security incident or system failure.
9. Monitoring and Logging: Utilize logging and monitoring tools to track network and system activities, enabling the detection of suspicious behavior and facilitating forensic analysis if security incidents occur.
10. Staff Training: Provide adequate training to staff on cybersecurity best practices, customer privacy, incident response procedures, and how to recognize and respond to security threats.
13. What is botnet? How it works?
The words “robot” and “network” together give rise to the term Botnet. Botnet refers to a network of hijacked internet-connected devices that are installed with malicious codes known as malware. Each of these infected devices is known as Bots, and a hacker/cybercriminal known as the “Bot herder” remotely controls them. A bot is also called a zombie, and a botnet is referred to as a zombie army.
How it works:
- Prepping the Botnet Army: The first step in creating a botnet is to infect as many connected devices as possible, to ensure that there are enough bots to carry out the attack. It uses the computing power of the infected devices for tasks that remain hidden to the device owners. However, the fraction of bandwidth taken from a single machine isn’t sufficient, and hence the Botnet combines millions of devices to carry out large-scale attacks. This way, it creates bots either by exploiting security gaps in software or websites or phishing emails. They often deploy botnets through a trojan horse virus.
- Establishing the connection: Once it hacks the device, as per the previous step, it infects it with a specific malware that connects the device back to the central botnet server. This way, it connects all the devices within the botnet network, and they are ready to execute the attack. A bot herder uses command programming to drive the bot’s actions.
- Launching the attack: Once infected, a bot allows access to admin-level operations like gathering and stealing user data, reading and writing system data, monitoring user activities, performing DDoS attacks, sending spam, launching brute force attacks, crypto mining.
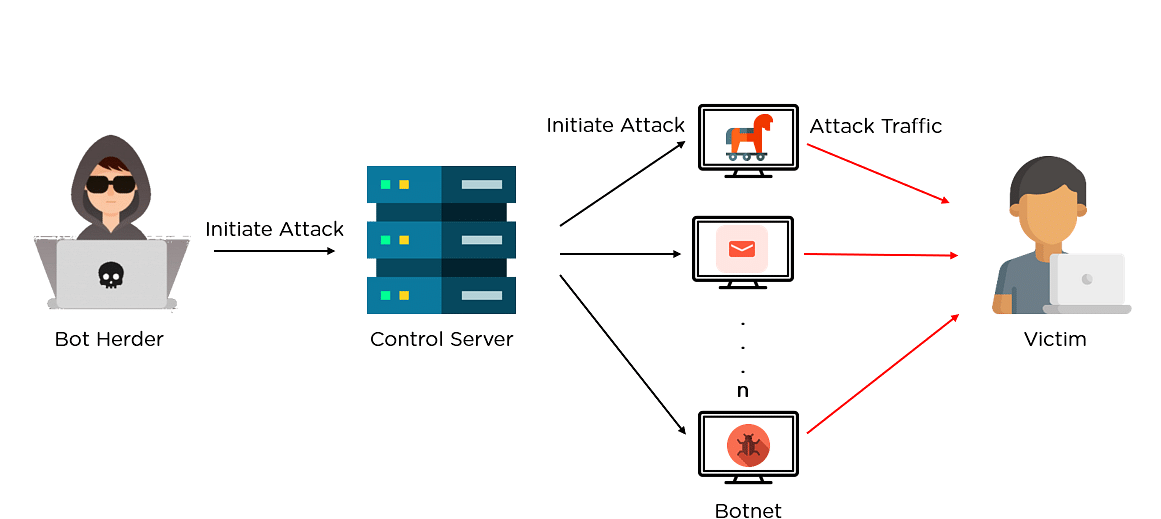
As seen in the above image, a bot herder initiates the attack by infecting several devices with malicious code, which acts as the Botnet. In the next step, these devices take over and conduct the final cyber attack. Therefore, even if you trace the cyberattack back in such a scenario, you cannot trace the bot herder easily.
In the next segment of this tutorial on what is a botnet, you will dive deeper into understanding botnets and look at the architecture of a botnet.
14. Explain cloud computing and cyber crime?
Cloud Computing:
Cloud computing refers to the use of hosted services, such as data storage, servers, databases, networking, and software over the internet. The data is stored on physical servers, which are maintained by a cloud service provider. Computer system resources, especially data storage and computing power, are available on-demand, without direct management by the user in cloud computing.
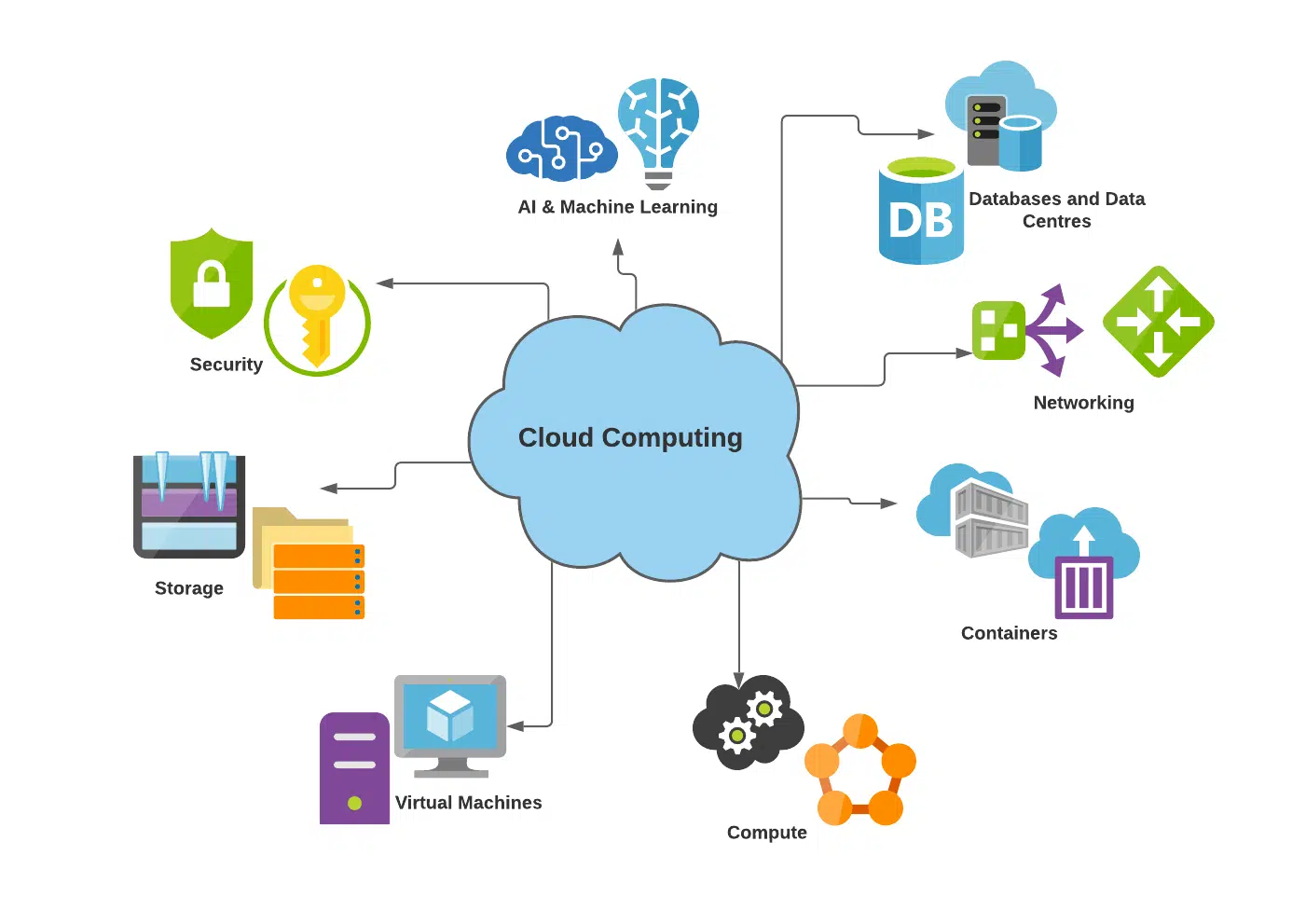
Characteristics of Cloud Computing:
On-Demand Self-Service: Users can provision computing resources, such as server instances or storage, as needed without requiring human interaction with each service provider.
Broad Network Access: Cloud services are available over the network and accessible through standard mechanisms (e.g., mobile phones, laptops, tablets).
Resource Pooling: The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand.
Rapid Elasticity: Cloud services can rapidly scale outward and inward to accommodate demand. Users can access as much or as little of a service as they need at any given time.
Measured Service: Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service.
Types of Cloud Services:
Infrastructure as a Service (IaaS): Offers virtualized computing resources over the internet. Users can rent IT infrastructure like virtual machines, storage, and networks.
Platform as a Service (PaaS): Provides a platform allowing customers to develop, run, and manage applications without the complexity of building and maintaining the infrastructure.
Software as a Service (SaaS): Delivers software applications over the internet on a subscription basis. Users can access the software through a web browser without installation.
Benefits of Cloud Computing:
Cost Savings: Cloud computing eliminates the need to invest in and manage physical infrastructure, reducing capital expenses.
Scalability: Cloud services can easily scale based on demand, allowing businesses to rapidly adapt to changing needs.
Flexibility: Users can access cloud services from anywhere with an internet connection, enabling remote work and mobile access.
Reliability: Cloud providers typically offer robust infrastructure and disaster recovery capabilities to maintain service availability.
Cybercrime:
Cybercrime is criminal activity that either targets or uses a computer, a computer network or a networked device. Most cybercrime is committed by cybercriminals or hackers who want to make money. However, occasionally cybercrime aims to damage computers or networks for reasons other than profit. These could be political or personal.
Cybercrime can be carried out by individuals or organizations. Some cybercriminals are organized, use advanced techniques and are highly technically skilled. Others are novice hackers. Types of cybercrime include:
Types of cybercrime include:
- Email and internet fraud.
- Identity fraud (where personal information is stolen and used).
- Theft of financial or card payment data.
- Theft and sale of corporate data.
- Cyberextortion (demanding money to prevent a threatened attack).
- Ransomware attacks (a type of cyberextortion).
- Cryptojacking (where hackers mine cryptocurrency using resources they do not own).
- Cyberespionage (where hackers access government or company data).
- Interfering with systems in a way that compromises a network.
- Infringing copyright.
- Illegal gambling.
- Selling illegal items online.
- Soliciting, producing, or possessing child pornography.
The different types of cyber crime include:
- Hacking: Gaining unauthorized access to a computer system or account, often to inflict further damage on the target
- Phishing: Impersonating legitimate companies or individuals to trick users into revealing sensitive information
- Malware: Spreading malicious software such as viruses, worms, Trojans, and ransomware within a device or network
- Identity theft: Stealing personal data such as names, addresses, and social security numbers to fraudulently assume someone’s identity
The Impact of Cyber Crime:
Cyber crime can affect individuals, businesses, and society in a variety of ways:
- Financial losses: Both individuals and businesses can suffer economic damage due to cyber crime. For example, a cyber attack that steals payment card information can lead to credit card fraud and identity theft.
- Personal effects: After a cyber attack, individuals may need to spend time protecting themselves and preventing further damage. Becoming a cyber crime victim can also be psychologically detrimental, resulting in anxiety and stress.
- Business disruption: Some cyber crimes, such as denial of service (DoS) attacks, are designed to disrupt a company’s operations for as long as possible. This can lead to website downtime, loss of customers and profits, and reputational damage.
- Public safety: Cyber criminals may target critical infrastructure such as power grids or manufacturing plants. This can disrupt essential services and even create risks to public safety.
15. Explain Proliferation (Growth) of Mobile and Wireless Devices?
The proliferation of mobile and wireless devices refers to the significant and rapid growth in the adoption and use of devices such as smartphones, tablets, wearables, and various IoT (Internet of Things) devices that connect wirelessly to networks.
This growth has been driven by several factors:
Technological Advancements: Advances in mobile and wireless technologies have led to the development of more powerful, feature-rich, and affordable devices. Improved connectivity standards such as 4G and 5G, as well as Wi-Fi advancements, have expanded the capabilities and appeal of mobile and wireless devices.
Increased Affordability: The widespread availability of mobile devices at various price points has made them more accessible to a broader range of consumers and businesses, driving increased adoption.
Enhanced Functionality: Mobile devices now offer a wide range of functionality, including communication, productivity, entertainment, and smart home control, making them indispensable in both personal and professional contexts.
Internet of Things (IoT) Growth: The proliferation of IoT devices, such as smart home appliances, connected vehicles, and industrial sensors, has contributed to the overall growth of wireless devices, extending connectivity and automation to various aspects of daily life and business operations.
Impact and Implications:
Ubiquitous Connectivity: The growth of mobile and wireless devices has led to a highly connected world, enabling instant communication, access to information, and continuous interaction with digital services.
Mobile Workforce: The widespread adoption of mobile devices has facilitated remote work, enabling individuals to stay connected and productive regardless of their location.
Digital Transformation: Businesses have embraced mobile and wireless technologies to enhance customer engagement, optimize operations, and develop innovative products and services.
Security Challenges: The increased use of wireless devices has expanded the attack surface for cyber threats, requiring robust security measures to protect sensitive data and systems.
Data Privacy Concerns: With the increasing volume of personal and corporate data being accessed and stored on mobile devices, privacy and data protection issues have come to the forefront.
Network Congestion: The proliferation of wireless devices has strained network infrastructure, demanding continuous upgrades to maintain quality of service and accommodate increasing data traffic.
As the proliferation of mobile and wireless devices continues, it is important for individuals and organizations to ensure robust security measures, effective device management, and responsible handling of sensitive data to mitigate associated risks and leverage the myriad benefits these technologies offer.
16. Write a short note on trends in mobility?
The trends in mobility are rapidly evolving, driven by technological advancements and changing consumer and business needs. Some notable trends in mobility include:
Electric Vehicles (EVs): The increasing focus on sustainability and environmental concerns is driving the adoption of electric vehicles. Technological advancements in battery technology and charging infrastructure are making EVs more practical and appealing to consumers.
Autonomous Vehicles: The development of self-driving cars and autonomous vehicle technology is revolutionizing the automotive industry. These vehicles have the potential to improve road safety, reduce traffic congestion, and provide greater mobility for individuals with limited transportation options.
Shared Mobility: The rise of ride-sharing services, bike-sharing programs, and scooter rentals is reshaping urban transportation. Shared mobility models offer cost-effective and convenient alternatives to traditional car ownership, promoting sustainability and reducing traffic congestion.
Connectivity and IoT: The integration of Internet of Things (IoT) technologies into transportation systems is enabling enhanced connectivity between vehicles, infrastructure, and digital platforms. This connectivity facilitates real-time data exchange, predictive maintenance, and improved traffic management.
Mobility as a Service (MaaS): MaaS platforms are integrating various transportation services, such as public transit, ride-sharing, and bike rentals, into a single, accessible platform. MaaS aims to provide more efficient, seamless, and personalized mobility solutions for users.
Micromobility: The growing popularity of electric scooters, e-bikes, and other compact, electric-powered vehicles is expanding the range of options for short-distance travel within urban areas.
17. What are the different types of attacks against 3G mobile networks?
Mobile 3G network attacks are attacks that are specifically targeted at 3G mobile networks. 3G, or third-generation, mobile networks are the third generation of mobile communication technology and are used to provide wireless data and voice services to mobile devices. There are several types of attacks that can be launched against 3G mobile networks, including eavesdropping, man-in-the-middle attacks, denial of service (DoS) attacks, malware infections, and interference with communication signals. It’s important for mobile network operators to implement security measures to protect against these types of attacks and keep their networks secure.
Types of 3G Mobile Attack
There are several types of attacks that can be launched against mobile networks:
Eavesdropping − This type of attack involves intercepting and listening to the communication between two parties without their knowledge.
Man-in-the-middle attack − In this type of attack, an attacker intercepts the communication between two parties and poses as one of the parties, allowing them to alter the communication and potentially steal sensitive information.
Denial of service (DoS) attack − A DoS attack involves flooding a network or device with traffic, making it unavailable to legitimate users.
Malware − Malware, or malicious software, can be used to compromise the security of a mobile network and steal sensitive information.
Interference − Attackers can interfere with the communication between two parties by disrupting the signals used to transmit data.
Rogue base stations − An attacker can set up a fake base station to intercept communication between mobile devices and the legitimate network.
SMS spoofing − Attackers can send text messages from a fake or spoofed sender, potentially tricking users into divulging sensitive information or downloading malware.
Location tracking − An attacker can track a mobile device’s location by accessing the location data transmitted by the device.
It’s important for mobile network operators to implement security measures to protect against these types of attacks and keep their networks secure.
18. Write a short note on Credit Card Frauds in Mobile and Wireless Computing Era?
Credit card fraud in the mobile and wireless computing era poses significant challenges as digital transactions become increasingly prevalent. The convergence of mobile devices, wireless connectivity, and online commerce has created new opportunities for fraudsters to exploit vulnerabilities. Some key considerations regarding credit card fraud in this context include:
Mobile Payment Security: The proliferation of mobile payment apps and digital wallets introduces new security concerns, such as unauthorized access to payment credentials, intercepted transactions, and compromised mobile payment platforms.
Phishing and Social Engineering: Fraudsters may employ phishing tactics via mobile channels, such as text messages or fake mobile apps, to trick users into disclosing sensitive credit card information or login credentials.
Data Interception: Unsecured wireless networks and public Wi-Fi hotspots can be susceptible to data interception, potentially exposing credit card details and transaction data to eavesdropping attacks.
Some common types of credit card fraud:
Lost or Stolen Devices: If a mobile device containing credit card information is lost or stolen, unauthorized individuals may attempt to use the stored data for fraudulent transactions.
Mobile Payment Account Takeover: Fraudsters can gain unauthorized access to a user’s mobile payment account, potentially making unauthorized purchases or transferring funds without the owner’s consent.
Card-Not-Present (CNP) Fraud: This occurs when fraudsters use stolen credit card details to make purchases online or through mobile apps where the physical card is not required, often relying on compromised credentials or stolen card information.
SMS Phishing (Smishing): Fraudsters may send deceptive text messages to mobile users, impersonating legitimate entities to trick them into divulging credit card details or clicking on malicious links that can compromise their information.
Mobile Wallet Fraud: Fraudulent activities involving mobile wallet platforms, such as unauthorized transactions or account takeovers, can occur due to compromised login credentials, social engineering, or security vulnerabilities.
Skimming and Cloning: In cases where mobile devices are used as payment terminals, skimming devices or unauthorized apps may capture credit card information, leading to unauthorized cloning of cards for fraudulent use.
Avoid Credit Card Fraud?
There is nothing to be afraid of. Here are some of the tips that you should follow to steer clear of credit card fraud.
- Keep Your Card Safe: The primary step is to keep your card in a safe place so that it is not easily accessible to others. After swiping your credit card, always check if the magnetic strip or back of the card is hampered in any way.
- Monitor Online Transaction: Most banks send an alert SMS after every online transaction. Another way of tracking your transactions is by installing your bank’s app. It helps you check your account balance and other details whenever needed.
- Review Billing Statements: To prevent different types of credit card fraud, one basic thing you should do is review your billing statements. This will allow you to note if any unknown or unauthorized transaction has been reported.
- Avoid Paper Trials: Another easy step that can prevent credit card scams is by shredding your billing statements. Credit card statements generally contain the full credit card number, so when you want to discard them, ensure shredding the document.
- Signing Blank Receipts: While signing credit card receipts, ensure the amount is verified. If you notice any blank spaces, make sure to cross-check with your bank regarding this.
- Never Make It Public: Your credit card details are very sensitive, so always beware of phishing. You must never share your card number, CVV or PIN through any text messages. Keep it memorized and also keep changing it after an interval.
19. Explain the Types and Techniques of Credit Card Frauds?
Credit card fraud encompasses various types and techniques that cybercriminals employ to unlawfully obtain financial information and conduct unauthorized transactions. Here are some common types and techniques of credit card fraud:
Card Skimming: Criminals use devices called skimmers to covertly capture credit card information when the card is swiped at ATMs, gas station pumps, or point-of-sale terminals. The stolen data is then used to create counterfeit cards or for online transactions.
Account Takeover: This involves cybercriminals gaining unauthorized access to a victim’s existing credit card account by stealing login credentials or personal information, allowing them to make illicit purchases or transfers.
Card Not Present (CNP) Fraud: CNP fraud occurs when stolen credit card information is used for online or over-the-phone transactions. Cybercriminals obtain card details through various means, such as data breaches or phishing scams, and exploit them to make purchases without the physical presence of the card.
Identity Theft: Fraudsters may use stolen personal information, including Social Security numbers, to open new credit card accounts in the victim’s name, thereby accumulating debt or making fraudulent transactions.
Malware-Enabled Fraud: This involves the use of malicious software to steal credit card information from compromised devices, intercept online transactions, or conduct unauthorized transfers from banking accounts.
Account Number Generation: Cybercriminals can use algorithms to generate valid credit card numbers, then use trial and error to determine which generated numbers are linked to active accounts. Once successful, they can use the stolen information for fraudulent transactions.
To combat credit card fraud, financial institutions and individuals can implement security measures such as EMV chip technology, tokenization, multi-factor authentication, transaction monitoring, and fraud detection systems. Additionally, consumer awareness, prompt reporting of unauthorized transactions, and vigilance against phishing attempts contribute to reducing the risk of falling victim to these fraudulent activities.
20. Write a short note on
a) Mobile phone theft
To address mobile phone theft, here are some key considerations:
Secure your device: Utilize built-in security features such as PIN codes, biometric authentication, and remote locking capabilities to protect the data on your device in the event of theft.
Activate tracking and remote wipe: Many smartphones offer options for remote tracking and data wiping in case of theft. Ensure these features are enabled to locate your device or remotely erase its data to prevent unauthorized access.
Report the theft: Immediately inform local law enforcement and your mobile service provider about the theft. Providing them with details such as the device’s unique identifier (IMEI), serial number, and any tracking information can aid in recovery efforts.
Notify your financial institutions: If your phone was used for mobile banking or contains payment apps, contact your bank and other financial institutions to report the theft and secure your accounts.
Consider insurance: Mobile phone insurance can provide coverage for theft, potentially alleviating the financial burden of replacing a stolen device.
Preventive measures: Be cautious in public spaces, avoid leaving your phone unattended, and consider using physical deterrents such as phone lanyards or anti-theft cases.
In some regions, mobile carriers and government agencies may provide databases or services to register stolen phones, making it more difficult for thieves to sell or activate stolen devices. Being proactive in safeguarding your device and promptly reacting to theft can mitigate the potential impact of mobile phone theft.
b) Mobile viruses
Mobile viruses are malicious software programs specifically designed to infect mobile devices, including smartphones and tablets, with the intent to steal data, damage the device, or exploit vulnerabilities for various malicious purposes. Here are some key points about mobile viruses:
Distribution: Mobile viruses can spread through various channels, such as infected apps, malicious links or attachments in emails or text messages, compromised websites, and even through Bluetooth or Wi-Fi connections.
Impact: Once a mobile device is infected, the virus can carry out a range of harmful activities, including stealing sensitive information (such as passwords or financial data), tracking user activities, sending unauthorized messages or making calls, and disrupting the normal functioning of the device.
Types of Mobile Malware: In addition to viruses, other types of mobile malware include trojans, which appear to be legitimate apps but carry out malicious activities, ransomware that encrypts or locks a device’s data for extortion, and adware that inundates the user with unwanted advertisements.
Protection: To protect against mobile viruses, users should take precautions such as installing reputable antivirus software, keeping the device’s operating system and apps updated, avoiding downloading apps from untrusted sources, being cautious about clicking on unknown links, and using secure Wi-Fi networks.
Security Measures: Mobile device manufacturers and operating system developers continuously incorporate security features like app sandboxing, secure boot, and facial recognition to mitigate the risk of mobile malware.
For businesses, implementing mobile device management (MDM) solutions and enforcing security policies can help minimize the risk of mobile virus infections across a mobile device fleet.
By staying informed about potential threats and taking proactive security measures, users can reduce the risk of falling victim to mobile viruses and safeguard their personal and sensitive data.
21. Write a note on
a) Mishing
Phishing by text messaging. The misher typically poses as an employee from the bank claiming they need your personal details or requesting that you settle an issue at their bank. With texting so prevalent in society, it was only a matter of time before thieves took to this method. Users may be more vulnerable to mishing if they purchase items using their phone or do mobile banking.
No doubt, protecting your identity is paramount with so many fraudulent activities in play, and protecting yourself from known activity increases the chances that you won’t fall victim.
Mishing, short for “mobile phishing,” is a form of cyber attack that targets mobile device users through deceptive messages. Here are the key points about Mishing in cybersecurity:
Targeted Approach: Mishing involves the use of text messages or SMS (Short Message Service) to deceive recipients into divulging sensitive information or to perform certain actions, such as clicking on malicious links or downloading harmful content.
Social Engineering: Mishing often relies on social engineering tactics, where attackers impersonate legitimate entities, such as banks, service providers, or government agencies, to create a sense of urgency or concern, prompting users to act quickly without thoroughly verifying the legitimacy of the message.
Risks: If successful, Mishing attacks can lead to the compromise of personal information, financial losses, unauthorized account access, or the installation of malware onto the victim’s mobile device.
Prevention: Users can mitigate the risk of Mishing by being cautious of unsolicited messages, examining URLs before clicking on them, avoiding sharing sensitive information via SMS, and using multi-factor authentication where possible.
Education: Organizations can also play a role in preventing Mishing attacks by educating their employees and customers about the signs of Mishing attempts and emphasizing the importance of verifying the authenticity of requests for sensitive information.
b) Vishing
Vishing, which stands for “voice phishing,” is a type of cyber attack that involves the use of voice communication, such as telephone calls, to deceive individuals into divulging sensitive information or performing certain actions. Here are the key points about Vishing in cybersecurity:
Approach: Vishing typically involves attackers using automated voice messages or engaging in live conversations to impersonate legitimate entities, such as financial institutions, government agencies, or tech support, and deceive victims into providing personal, financial, or security information.
Social Engineering: Vishing attacks rely on social engineering tactics, exploiting psychological manipulation and the perception of authority or urgency to convince individuals to disclose confidential information, such as account credentials, social security numbers, or payment details.
Risks: If successful, Vishing attacks can lead to identity theft, financial fraud, unauthorized access to sensitive accounts, and potential compromise of personal or corporate data.
Prevention: To mitigate the risk of Vishing, individuals should be cautious of unsolicited calls, especially those requesting sensitive information. Verifying the legitimacy of the caller and the purpose of the call before providing any information is crucial in preventing Vishing attacks.
Security Awareness: Organizations can enhance Vishing prevention through employee training, emphasizing the importance of never disclosing sensitive information over the phone unless the caller’s identity and purpose have been verified.
By maintaining vigilance and following best practices for verifying the authenticity of calls and protecting sensitive information, individuals and organizations can reduce the likelihood of falling victim to Vishing attacks and protect against potential security breaches.
c) Smishing
Smishing, a portmanteau of “SMS” and “phishing,” refers to a type of cyber attack that involves the use of SMS (Short Message Service) or text messaging to deceive individuals into divulging sensitive information, clicking on malicious links, or downloading harmful content. Here are the key points about Smishing in cybersecurity:
Modus Operandi: Smishing attacks typically utilize text messages that impersonate legitimate entities, such as banks, retailers, or service providers, and prompt recipients to take actions that can compromise their security, such as clicking on fraudulent links or providing sensitive personal or financial information.
Social Engineering: Similar to phishing and vishing, Smishing relies on social engineering tactics to create a sense of urgency, importance, or alarm to persuade individuals to act hastily without verifying the authenticity of the message.
Risks: If successful, Smishing attacks can lead to various security breaches, including identity theft, financial fraud, unauthorized access to accounts, and the installation of malware on the recipient’s mobile device.
Prevention: To reduce the risk of falling victim to Smishing, individuals should exercise caution when receiving unsolicited text messages, avoid clicking on links from unknown or unverified sources, and refrain from providing sensitive information via text unless the message’s legitimacy has been verified.
Security Measures: Organizations can play a role in combating Smishing by educating their employees and customers about the signs of Smishing attempts and the importance of exercising caution when responding to text messages containing requests for confidential information.
By remaining attentive, scrutinizing incoming text messages, and verifying the authenticity of requests for information, individuals can mitigate the risk of falling victim to Smishing attacks and safeguard their personal and financial data.
22. Discuss about Authentication Service Security?
Authentication is the procedure of recognizing someone’s identity by assuring that the person is the similar as what it is claiming for. It can be used by both server and client.
The server uses authentication when someone needs to access the data, and the server required to understand who is accessing the data. The client uses it when it is need to understand that it is the same server that it claims to be.
The authentication by the server is completed mostly by utilizing the username and password. There are some another method of authentication by the server can also be completed using cards, retina scans, voice identification, and fingerprints.
Authentication does not provide what service under a process one person can do, what document it can view, read, or update. It mainly recognizes who the person or system is absolutely.
Modern computer systems provide service to multiple users and require the ability to accurately identify the user making a request.
Password based authentication is not suitable for use on computer network – as it can be easily intercepted by the eavesdropper to impersonate the user.
There are 2 components of security in mobile computing:
- Security of Devices: A secure network access involves mutual authentication between the device and the base station or web servers. So that authenticated devices can be connected to the network to get requested services. In this regard Authentication Service Security is important due to typical attacks on mobile devices through WAN:
- DoS attacks:
- Traffic analysis:
- Eavesdropping:
- Man-in-the-middle attacks:
- Security in network: Security measures in this regard come from
- Wireless Application Protocol (WAP)
- use of Virtual Private Networks (VPN)
- MAC address filtering
Authentication service security is a critical aspect of cybersecurity, as it directly impacts an organization’s ability to verify the identity of users and protect sensitive information. Here are some key aspects of authentication service security:
Strong Authentication Methods: Implementing strong authentication methods, such as multi-factor authentication (MFA), biometrics, hardware tokens, and one-time passwords, can significantly enhance the security of authentication services by requiring multiple forms of verification to access sensitive systems and data.
Encryption: Utilizing encryption for authentication data, including user credentials and authentication tokens, helps safeguard this information from unauthorized access or interception by malicious actors.
Access Control: Robust access control mechanisms should be in place to restrict user access to sensitive resources based on their roles, privileges, and the principle of least privilege, ensuring that individuals only have access to the resources necessary for their responsibilities.
User Identity Management: Proper user identity management, including regular review and updating of user accounts, password policies, and the deactivation of inactive accounts, is essential to prevent unauthorized access and maintain the integrity of the authentication service.
Secure Protocols: The use of secure communication protocols, such as Transport Layer Security (TLS), for authenticating and validating user identities helps protect against eavesdropping and man-in-the-middle attacks during the authentication process.
Monitoring and Logging: Implementing robust monitoring and logging capabilities allows for the detection of unauthorized access attempts, unusual authentication patterns, and potential security incidents, enabling timely responses and forensic analysis.
Regular Audits and Assessments: Conducting regular security audits and assessments of the authentication service helps identify vulnerabilities, weaknesses, and compliance issues, allowing for the implementation of necessary improvements and ensuring alignment with industry best practices and regulatory requirements.
User Education: Educating users about best practices for creating secure passwords, recognizing phishing attempts, and understanding the importance of authentication security contributes to a more secure authentication environment.
23. What are different security challenges posed by mobile devices? Explain?
Mobile devices present several security challenges due to their portability, connectivity, and the potential for containing sensitive data. Here are some of the key security challenges posed by mobile devices:
Data Loss and Theft: The small form factor and portability of mobile devices make them susceptible to loss or theft, leading to the potential compromise of sensitive data if not properly protected.
Unauthorized Access: Inadequate authentication measures or the lack of device encryption can result in unauthorized individuals gaining access to the device and its data, potentially leading to data breaches and privacy violations.
Malware and Vulnerabilities: Mobile devices are susceptible to malware, including viruses, ransomware, and spyware, which can compromise the integrity of the device, steal data, or enable unauthorized access to confidential information.
Network Security Risks: Mobile devices often connect to various networks, including public Wi-Fi, increasing the risk of interception, man-in-the-middle attacks, and exposure to malicious entities seeking to exploit vulnerabilities in network communications.
Phishing and Social Engineering: Mobile users are susceptible to phishing attacks through fake websites, emails, or SMS messages, potentially leading to the disclosure of sensitive information and the compromise of login credentials.
Device Fragmentation: The diverse range of mobile operating systems, versions, and device types can lead to fragmentation, making it challenging for organizations to maintain consistent security standards and deploy patches and updates uniformly across devices.
BYOD (Bring Your Own Device): The adoption of BYOD policies introduces additional security challenges, as personal devices may not adhere to the same security standards as corporate-managed devices, potentially exposing sensitive corporate data to risk.
Lack of User Awareness: Users may inadvertently compromise the security of their devices through unawareness of best practices, such as connecting to unsecured networks or downloading malicious apps.
Physical Security: The potential for physical access to mobile devices, whether intentionally or unintentionally, poses a security challenge, as unauthorized individuals may extract data or compromise device integrity.
Addressing these security challenges requires a comprehensive approach, including the implementation of strong authentication methods, encryption of data in transit and at rest, regular security patching and updates, mobile device management (MDM) solutions, security awareness training for users, and the enforcement of BYOD security policies. Additionally, the use of mobile security solutions, such as mobile device management (MDM), mobile threat defense (MTD), and secure containers, can help mitigate the risks associated with mobile device usage.
24. Explain Bluetooth hacking tools and various types of Bluetooth attacks?
The term “Bluetooth Hacking” refers to a kind of cyberattack in which hackers obtain access to a target device by exploiting its discoverable Bluetooth connection. This event occurs as a result of security weaknesses in Bluetooth technology. It’s not only mobile phones that may be hacked through Bluetooth; PCs of all shapes and sizes can be compromised similarly.
Bluetooth hacking can range from eavesdropping on conversations and stealing sensitive data to taking control of devices, spreading malware, or conducting denial-of-service attacks. It is important to note that Bluetooth hacking is illegal and unethical, as it violates the privacy and security of individuals and organizations. It is crucial to implement proper security measures, such as using strong authentication and encryption, to protect against Bluetooth hacking attempts.
Types:
The following is a list of the many hacking tactics that hackers can use to infiltrate your Bluetooth and steal your sensitive data. Here are the various types of Bluetooth attacks –
BlueSmacking
BlueJacking
BlueBugging
BlueSnarfing
1. BlueSmacking: A cyberattack called Bluesmack targets Bluetooth-enabled gadgets. The assault sends an excessively large packet to Bluetooth-enabled devices via the L2CAP (Logic Link Control and Adaptation Protocol) layer, which causes a Denial of Service (DoS) attack.
2. BlueJacking: Using the hacking technique known as “bluejacking,” a person can send unwanted messages—often flirty but occasionally malicious—to any Bluetooth-enabled device in his or her line of sight. The procedure, called “bluejacking,” starts with searching nearby Bluetooth-enabled devices
3. BlueBugging: Hackers use Bluebugging to easily access a device when it is in “discovery mode,” or while Bluetooth is enabled. Hackers use Bluebugging to get access to calls, read and send text messages, steal crucial information stored on the device, and even redirect incoming calls to their own numbers. Although laptops were the primary target of bluebugging, hackers soon found ways to exploit the vulnerability in any device that utilized Bluetooth. The attack was developed after the emergence of bluejacking and bluesnarfing.
4. BlueSnarfing: Bluesnarfing refers to the illegal acquisition of sensitive data over Bluetooth. Hackers access networks by infiltrating users’ unprotected mobile devices, such as cell phones, laptops, tablets, and PDAs. It entails taking advantage of Bluetooth flaws to steal information, including text messages, emails, contact lists, and more.
Bluetooth Hacking Tools:
Here are some commonly used Bluetooth hacking tools:
- BlueScanner: This tool enables to search for Bluetooth enabled devices and will try to collect as much information as possible for each newly discovered device after connecting it with the target.
- BlueSniff: It is a GUI-based tool for locating Bluetooth-enabled devices that are both discoverable and concealed.
- BlueBugger: The attackers take advantage of the device’s weakness to access photos, the phonebook, messages, and other private data.
- Bluesnarfer: When a device’s Bluetooth is turned ON, Bluesnarfing enables a connection to the phone without the owner’s knowledge and allows access to certain parts of the stored data.
- BlueDiving: Bluediving tests the penetration of Bluetooth. Attacks like Bluebug and BlueSnarf are implemented by it.
25. What are the physical security counter measures for laptop?
Physical security countermeasures for laptops are essential to prevent unauthorized access, theft, and the compromise of sensitive data. Here are some effective physical security countermeasures for laptops:
Laptop Locks: Utilize cable locks that can be secured to a stationary object, such as a desk or table, to prevent opportunistic theft of laptops in public spaces or office environments.
Secure Storage: When not in use, store laptops in locked cabinets, drawers, or secure laptop bags to prevent unauthorized access or potential theft.
Access Control: Implement access control measures to restrict physical access to areas where laptops are stored or used, such as using keycard entry, biometric locks, or security personnel to monitor access.
Asset Tracking: Employ asset tracking and inventory management systems to keep a record of all laptops, including their location, assigned users, and maintenance history to ensure accountability and facilitate recovery in case of theft.
Security Awareness: Educate employees and users about the importance of physical security and provide guidelines for safeguarding laptops, including avoiding leaving them unattended in public spaces or vehicles.
Secure Transportation: When transporting laptops, use secure and inconspicuous bags or cases to avoid drawing attention to the presence of valuable electronic devices.
Secure Workstations: Encourage the use of locking mechanisms or security brackets to secure laptops to desks in office environments, reducing the risk of opportunistic theft.
Privacy Screens: Utilize privacy screens or filters to prevent unauthorized viewing of laptop screens in public locations, maintaining the confidentiality of on-screen information.
26. What are different Registry Settings for Mobile Devices? Explain? [10Marks]
The term “registry settings” is typically associated with Microsoft Windows operating systems, where the Windows Registry serves as a centralized database for storing configuration settings and options for the operating system and installed applications. However, in the context of mobile devices such as smartphones and tablets, the concept of a registry is not typically applicable in the same way.
Instead, mobile devices, particularly those running operating systems such as iOS (Apple), Android (Google), and others, utilize different mechanisms for managing settings and configurations. These may include:
Settings App: Mobile devices have a settings application or menu where users can adjust various device settings such as Wi-Fi, Bluetooth, display, notifications, privacy, and security settings.
Configuration Profiles: Mobile device management (MDM) solutions and enterprise environments may deploy configuration profiles to enforce specific settings, restrictions, and security policies on mobile devices. These profiles can control a wide range of settings, including email and VPN configurations, passcode requirements, and app permissions.
App-specific Settings: Individual mobile applications often have their own settings or preferences within the app itself, allowing users to customize their experience and manage app-specific configurations.
Developer Options: For Android devices, there are developer options that provide advanced settings for debugging, performance tuning, and software development activities.
Accessibility Settings: Both iOS and Android devices offer accessibility settings to cater to users with diverse needs, including options for vision, hearing, motor skills, and cognitive functions.
Security and Privacy Settings: Mobile devices have specific settings related to security, such as device encryption, biometric authentication, app permissions, and privacy controls, which users can configure based on their preferences and security needs.
It’s important to note that the settings and configuration options available on mobile devices are specific to the operating system and the device manufacturer. For example, settings on an iPhone running iOS will differ from those on a Samsung device running Android. Additionally, the specific terminology and organization of these settings can vary widely between different operating systems and versions.
While the concept of “registry settings” does not directly apply to mobile devices in the same way it does to Windows-based systems, various settings and configurations are available on mobile devices through built-in menus, configuration profiles, app settings, and developer options.
27. Discuss about the Security implications for Organizations?
The security implications for organizations in the context of mobile/cell phone attacks are significant and multifaceted, as the increasing adoption of mobile devices in the workplace introduces new challenges and risks. Some key security implications include:
Data Breaches: Mobile/cell phone attacks can lead to data breaches, compromising sensitive corporate information, intellectual property, customer data, and employee records. This can result in financial losses, legal liabilities, and reputational damage for the organization.
Regulatory Compliance: Organizations may be subject to regulatory requirements related to the protection of sensitive data, such as the General Data Protection Regulation (GDPR) in the European Union or the Health Insurance Portability and Accountability Act (HIPAA) in the United States. Mobile security incidents and data breaches can lead to non-compliance and potential legal consequences.
Business Continuity: Mobile attacks can disrupt business operations by compromising access to critical systems and data, leading to downtime, productivity losses, and impaired service delivery. This can have direct financial implications and damage customer trust.
Intellectual Property Theft: Attacks targeting mobile devices can result in the theft of intellectual property, including proprietary information, research and development data, and strategic plans, posing a threat to an organization’s competitive advantage and innovation.
Reputation Damage: Security incidents involving mobile devices can erode stakeholder trust, damage the organization’s reputation, and impact customer and partner relationships. A publicized breach can lead to loss of business and diminished brand value.
Legal and HR Ramifications: Mobile security incidents may trigger legal and human resources implications, such as the need for legal action, regulatory reporting, and internal investigations, as well as potential implications for employee policies and responsibilities.
To address these security implications, organizations should consider implementing the following measures:
Mobile Device Management (MDM): Deploying MDM solutions to manage and secure corporate-owned and BYOD (Bring Your Own Device) mobile devices by enforcing policies, conducting remote device management, and implementing security controls.
Endpoint Security: Implementing robust endpoint security solutions on mobile devices to detect and prevent malware, unauthorized access, and data exfiltration, as well as enabling remote device wiping and monitoring capabilities.
Security Policies and Training: Establishing clear security policies governing mobile device usage, data handling, and access controls, while providing comprehensive security awareness training to employees to promote safe mobile practices.
Secure Network Access: Implementing secure access controls and using VPNs to ensure encrypted communication for mobile devices accessing corporate networks and sensitive data.
Incident Response Planning: Developing and regularly testing incident response plans specific to mobile security incidents to enable prompt and effective responses to potential breaches and compromises.
Regular Security Audits: Conducting regular security audits and assessments to identify vulnerabilities, monitor compliance, and address emerging mobile security risks.
28. What different Organizational measures for handling Mobile?
Organizations can implement several measures to effectively handle mobile devices and mitigate security risks. These measures encompass policies, technologies, and best practices to secure and manage mobile devices within the organizational environment. Here are some organizational measures for handling mobile devices:
Mobile Device Management (MDM): Implementing MDM solutions to centrally manage and secure mobile devices by enforcing security policies, configuring settings, distributing applications, and remotely monitoring and wiping devices if necessary.
Bring Your Own Device (BYOD) Policies: Establishing clear BYOD policies to govern the use of personal devices for work purposes, including security requirements, acceptable use guidelines, and procedures for separating personal and corporate data on employee-owned devices.
Mobile Application Management (MAM): Employing MAM solutions to manage and secure the life cycle of mobile applications, including app distribution, monitoring, and the enforcement of app-level security policies.
Multi-Factor Authentication (MFA): Implementing MFA solutions to add an extra layer of security to device and application access, requiring users to provide multiple forms of verification for authentication.
Encryption and Data Protection: Enforcing encryption of data at rest and in transit on mobile devices to safeguard sensitive information and mitigate the risk of unauthorized access or data theft.
Secure Network Access: Implementing secure network access controls and leveraging Virtual Private Networks (VPNs) to ensure encrypted communication for mobile devices accessing corporate resources and sensitive data.
Security Awareness Training: Providing comprehensive security awareness training to employees to educate them about mobile security best practices, common threats, and proper handling of corporate information on mobile devices.
Incident Response Planning: Developing and regularly testing incident response plans specifically tailored to handle mobile security incidents, including protocols for investigating, containing, and mitigating the impact of security breaches.
Regular Security Audits and Compliance Checks: Conducting periodic security audits, vulnerability assessments, and compliance checks to identify and address security gaps, ensure adherence to security policies, and stay abreast of emerging mobile security threats.
Continuous Monitoring and Threat Detection: Employing solutions for real-time monitoring of mobile device activities and implementing threat detection capabilities to identify and respond to potential security incidents swiftly.
Mobile Security Governance: Establishing a mobile security governance framework that defines roles, responsibilities, and accountability for mobile security across the organization, ensuring consistent and effective management of mobile security measures.
29. Explain about the Organizational Security policies for mobile devices?
Organizational security policies for mobile devices serve as a critical framework for mitigating security risks and establishing guidelines for the secure use of mobile technology within the organization. These policies encompass a set of rules, protocols, and best practices designed to protect sensitive data, prevent unauthorized access, and maintain the integrity of corporate assets. Here are key components of organizational security policies for mobile devices:
Device Usage Guidelines: Define acceptable use standards for mobile devices, outlining the permitted activities, responsibilities of employees, and guidelines for accessing corporate resources from mobile devices.
Device Management and Configuration: Specify requirements for the configuration, management, and security settings of mobile devices, including the installation of security updates, access controls, and the enforcement of encryption policies.
Bring Your Own Device (BYOD) Policies: Outline the rules and security measures for employees using personal devices for work purposes, including requirements for device security, data segregation, and compliance with corporate security policies.
Access Control and Authentication: Establish protocols for user authentication and access control on mobile devices, including the use of strong passwords, biometric authentication, and multi-factor authentication (MFA) to prevent unauthorized access.
Data Protection and Encryption: Define rules for the encryption of sensitive data at rest and in transit on mobile devices to safeguard against data breaches, unauthorized access, and data theft.
Network Security and VPN Usage: Specify guidelines for secure network access and the use of Virtual Private Networks (VPNs) to ensure encrypted communication when accessing corporate resources from mobile devices, particularly when connecting to unsecured networks.
Application Management: Set standards for the installation and usage of applications on mobile devices, including the prohibition of unauthorized or unvetted applications that could pose security risks.
Incident Reporting and Response: Outline procedures for reporting security incidents related to mobile devices and delineate the steps to be taken in the event of a security breach, including notification requirements and incident response protocols.
Security Awareness Training: Detail the requirements for ongoing security awareness training for employees, educating them about mobile security risks, best practices, and the handling of sensitive corporate information on mobile devices.
Regulatory Compliance: Ensure alignment with relevant data protection regulations, industry standards, and legal requirements related to the protection of sensitive data on mobile devices, such as GDPR, HIPAA, or the Payment Card Industry Data Security Standard (PCI DSS).
Enforcement and Monitoring: Specify the mechanisms for enforcing compliance with mobile security policies, conducting regular security audits, and monitoring mobile device activities to identify and mitigate potential security threats.
Bring Your Own Device (BYOD) Policies: Define and communicate the requirements and limitations for employees using their personal devices for work purposes, including expectations around data security, compliance with organizational policies, and any specific configurations or security measures required for personal devices used for work.
30. What are the different ways of password cracking?
Password cracking refers to the process of attempting to guess or recover a password from stored or transmitted data. There are several methods and techniques used for password cracking, each with varying levels of complexity and effectiveness. Here are some of the different ways of password cracking:
Brute Force Attack: This method involves systematically checking all possible combinations of characters until the correct password is found. Brute force attacks are generally time-consuming, especially for complex and lengthy passwords, but they are effective given enough time and computational resources.
Dictionary Attack: A dictionary attack involves using a list of commonly used passwords, words from dictionaries, and variations thereof to attempt to guess the password. This method is more efficient than brute force since it only tries likely passwords, but it is ineffective against complex and unique passwords.
Rainbow Table Attack: Rainbow tables are precomputed tables of hashed passwords, allowing for the rapid lookup of plaintext passwords corresponding to specific hashes. Attackers use rainbow tables to look up the hash of the stolen password and find a matching plaintext password.
Phishing: This method involves tricking users into revealing their passwords through deceptive means, such as fake login pages or fraudulent emails. Phishing attacks rely on social engineering tactics to manipulate individuals into divulging their credentials.
Keylogging: Keyloggers are malicious software or hardware that record keystrokes entered by a user. Attackers use keyloggers to capture passwords as they are typed, allowing them to retrieve the recorded keystrokes later.
Shoulder Surfing: This low-tech method involves visually observing a user entering their password, either in person or via video surveillance, to capture the password without the user’s knowledge.
Social Engineering: Social engineering techniques involve manipulating individuals into revealing their passwords through psychological manipulation or deception, often through pretexting, impersonation, or eliciting sensitive information.
Guessing: Attackers may attempt to guess passwords based on personal information about the target, such as their birthdate, family members’ names, or other commonly used information.
It is important for individuals and organizations to prioritize strong, unique passwords, employ multi-factor authentication, and implement robust security measures to mitigate the risk of password cracking attempts. Additionally, regular security awareness training can help users recognize and resist social engineering and phishing attempts.
31. Write about Mobile/Cell Phone attacks.
Mobile/cell phone attacks refer to malicious activities targeted at exploiting vulnerabilities in mobile devices, compromising the security and privacy of users, and potentially causing financial or reputational harm. These attacks can take various forms and target different components of mobile devices, including the operating system, installed applications, and communication channels. Some common types of mobile/cell phone attacks include:
Malware: Mobile malware includes viruses, worms, Trojans, and other types of malicious software designed to infect mobile devices. Malware can steal sensitive information, track user activities, send premium-rate SMS messages, or turn infected devices into bots for coordinated attacks.
Phishing: Attackers may use phishing techniques to trick mobile users into disclosing sensitive information such as passwords, credit card details, or personal data by masquerading as legitimate entities through fake websites, emails, or text messages.
Man-in-the-Middle (MitM) Attacks: MitM attacks intercept communication between a mobile device and a network, allowing attackers to eavesdrop on sensitive information, modify data in transit, or impersonate legitimate parties, potentially compromising the confidentiality and integrity of data transmissions.
Rogue Application: Attackers can create and distribute rogue applications that appear to be legitimate but contain malicious code designed to steal data, track user activities, or perform unauthorized actions on the device.
Network Spoofing: This attack involves setting up malicious Wi-Fi or cellular network hotspots to deceive mobile devices into connecting to them, enabling attackers to intercept data, perform man-in-the-middle attacks, or deliver malware to connected devices.
Social Engineering: Attackers may exploit human psychology to manipulate mobile users into performing actions that compromise their security, such as disclosing sensitive information, downloading malware, or granting excessive permissions to rogue applications.
To mitigate mobile/cell phone attacks, users can take proactive measures such as:
- Keeping operating systems and applications up to date to patch known vulnerabilities.
- Installing and regularly updating mobile security software to detect and remove malware.
- Exercising caution when clicking on links or downloading attachments from unknown or untrusted sources.
- Using strong, unique passwords and enabling multi-factor authentication for added security.
- Avoiding unsecured Wi-Fi networks and using virtual private networks (VPNs) for secure internet access.
- Being mindful of security and privacy settings when granting permissions to apps and services.
Mobile device manufacturers and network operators play a crucial role in addressing mobile/cell phone attacks by implementing robust security measures and regularly updating devices to protect against emerging threats. Ongoing user education and awareness about potential security risks are also essential for promoting safe mobile usage practices.
32. Explain the general guidelines applicable to the password policy.
Certainly! An effective password policy is crucial for enhancing the overall security posture of an organization’s information systems. Here are some general guidelines applicable to a robust password policy:
Password Length: The policy should specify a minimum password length to ensure complexity and resilience against brute force attacks. A common recommendation is to set a minimum password length of at least 8-12 characters.
Complexity Requirements: The policy should mandate the use of complex passwords containing a combination of uppercase and lowercase letters, numbers, and special characters. This can significantly increase the difficulty of password cracking attempts.
Password Expiration: Enforce regular password expiration intervals, prompting users to change their passwords at predefined intervals, such as every 60 or 90 days. Regular password changes can mitigate the risk of compromised credentials.
Prohibited Passwords: The policy should prohibit the use of easily guessable or commonly used passwords, such as “password,” “123456,” or the user’s name. Additionally, it should prevent the reuse of previously used passwords.
Multi-Factor Authentication (MFA): Encourage or mandate the use of multi-factor authentication (MFA) wherever possible to add an extra layer of security beyond passwords. This may include using SMS codes, authenticator apps, or biometric factors.
Account Lockout and Failed Login Attempts: Implement mechanisms for automatically locking out user accounts after a certain number of consecutive failed login attempts to prevent brute force attacks.
User Awareness and Training: Emphasize the importance of password security through user awareness training, teaching users how to create and manage strong passwords and recognize phishing attempts.
Secure Storage: Ensure that passwords are stored securely using industry-standard encryption techniques and strong hashing algorithms to protect them from unauthorized access.
Password Recovery: Establish secure procedures for password recovery that require additional verification steps to prevent unauthorized access to user accounts.
Access Control: Integrate password policy with broader access control measures, limiting unauthorized access to sensitive systems and data.
Regulatory Compliance: Ensure that the password policy aligns with relevant industry regulations and standards, such as GDPR, HIPAA, or PCI DSS, as necessary.
33. How can key loggers be used to commit a cybercrime?
Keyloggers can be used as a tool to commit various cybercrimes due to their ability to capture and record keystrokes entered by a user. Here are some ways in which keyloggers can be utilized for malicious purposes:
Password Theft: Keyloggers can capture usernames, passwords, and other sensitive authentication details entered by users. This information can be exploited to gain unauthorized access to online accounts, financial transactions, and confidential data.
Identity Theft: By capturing personal information such as Social Security numbers, credit card details, and other sensitive data, keyloggers can facilitate identity theft, which can result in financial losses and damage to an individual’s reputation and credit history.
Corporate Espionage: In the context of corporate environments, keyloggers can be used to steal sensitive company information, intellectual property, and confidential communications. This stolen information can be leveraged for competitive advantage by rival organizations or sold on the black market.
Monitoring Communications: Keyloggers can intercept and record emails, instant messages, and other forms of digital communication, providing cybercriminals with access to private conversations and confidential information.
Financial Fraud: Keyloggers can be used to capture financial transaction details, including online banking credentials, credit card information, and other payment processing data. This can result in financial fraud and unauthorized fund transfers.
Surveillance and Blackmail: Keyloggers can be used for covert surveillance, capturing sensitive or compromising information that can be used for blackmail or extortion purposes.
Industrial Sabotage: In industrial or organizational settings, keyloggers can be used to collect proprietary information, sabotage operations, or disrupt business activities.
34. What are the advantages of using anti-keylogger?
Advantage of using Anti-Keylogger:
- It helps to manage the activities of any keyLogger present in the system.
- If it identifies any keylogger, then it prevents its activity from saving the confidential information.
- It is not able to identify the types of keystrokes, which means it is not able to differentiate between the legal keystroke program and the illegal keystroke program.
- It is used by many companies and especially in public computers, to stop the keyLogger activities.
- It supports current and future cybersecurity threats.
- Some anti-keyloggers provide no delay while typing.
- Easily integrate with C++ libraries.
The disadvantage of using an Anti-keylogger:
- Not differentiating any keylogger activity can also act as a disadvantage. That is not differentiating between a legal keystroke program with an illegal keystroke program.
35. What is the difference between a virus and a worm?
| Virus | Worm |
| A computer virus is a program, where a code reproduces itself and then replicates itself to other programs. | A computer worm is an independent or free malicious program |
| The viruses need hosts to spread from one system or device to another. | Worms however do not need any host. |
| Its spreading speed is slower. | Its spreading speed is faster. |
| Viruses can’t be controlled by remote. | Worms can be controlled by remote. |
| It is more harmful. | It is less harmful as compared. |
| Viruses are executed via executable files. | Worms are executed via weaknesses in the system. |
| The virus spreads at a comparatively slower pace than a Worm. | A worm can quickly spread through a device and it can infect many devices or networks quickly. |
| The main purpose of the virus is to transform or modify the information. | The main aim of worms is to eat the system resources. |
| Some of the examples of computer viruses are; Creeper, Blaster, Slammer, etc. | Some of the examples of computer worms are Morris worm, storm worm, etc. |
| Antivirus software is employed for protection against viruses. | Worms can be identified and eliminated by the Antivirus and firewall. |
| The full form of the Virus is Vital Information Resources Under Siege. | Worms stand for Write-Once, Read-Many. |
| Viruses are executed through executable files/data. | Worms are executed through weaknesses in the system. |
36. What are the different types of viruses? Explain in details.
Viruses are malicious software programs designed to replicate and spread by infecting computer systems and devices, causing harm to data, software, or the system itself. There are several different types of computer viruses, each with distinct characteristics and methods of propagation. Here are the most common types of computer viruses:
File Infector Viruses: These viruses attach themselves to executable files, such as .exe or .com files, and infect them. When the infected file is executed, the virus gains control and infects other files on the system. File infector viruses can cause widespread damage by compromising critical system files and applications.
Macro Viruses: Macro viruses are embedded within document files, such as Word or Excel documents, and are typically spread through email attachments or file sharing. Once the infected document is opened, the macro virus can execute malicious actions, such as modifying or deleting files, and spread to other documents.
Boot Sector Viruses: These viruses target the boot sector of storage devices like hard drives or flash drives. When the infected device is booted, the virus loads into the computer’s memory and can infect the system, leading to data loss, system instability, or unauthorized access.
Resident Viruses: Resident viruses embed themselves into a computer’s memory, allowing them to remain active even after the initiating program is terminated. These viruses can infect files as they are opened or executed, making them challenging to detect and remove.
Polymorphic Viruses: Polymorphic viruses are designed to evade detection by changing their code each time they infect a new file or system. This mutation makes them difficult to identify using traditional antivirus techniques, increasing their effectiveness at bypassing security measures.
Worms: Unlike traditional viruses, worms can replicate and spread independently, typically by exploiting vulnerabilities in networked systems. They can propagate rapidly across interconnected computers and networks, causing significant disruption and potential damage to data and infrastructure.
Trojans: Trojans disguise themselves as legitimate software to trick users into executing them. Once activated, trojans can perform various malicious actions, such as data theft, unauthorized access to the system, and facilitating the installation of other types of malware.
Ransomware: Ransomware encrypts a user’s files or locks the system, demanding a ransom payment in exchange for restoring access. Ransomware attacks can cause severe data loss and financial impact, making them particularly devastating for individuals and organizations.
Spyware: Spyware silently collects and transmits a user’s personal information, including browsing habits, login credentials, and financial data, to a remote attacker. This poses significant privacy and security risks.
