CF 2022 Regular (NEP) Questions with Answers
Section - A
1. Answer any Six question.
a. What is output device? Give example.
An output device is any piece of computer hardware that converts information/DATA into a human-perceptible form or, historically, into a physical machine-readable form for use with other non-computerized equipment. It can be text, graphics, tactile, audio, or video.
Examples of output devices:
- Monitors: Monitors display text, images, and videos.
- Printers: Printers print text and images onto paper.
- Speakers: Speakers produce sound.
- Headphones: Headphones produce sound that is only heard by the wearer.
- Projectors: Projectors project images and videos onto a large screen or wall.
b. Name any two digital computers.
- Mainframes
- Supercomputers
- Embedded systems
- Personal computers (PCs)
c. 25(15)=__________________(2)?
101110111 in binary.
d. Define compiler.
A compiler is a computer program that translates code written in one programming language (the source language) into another language (the target language). The target language is often a machine code, which is the code that the computer can directly execute.
e. What is Application program ? Give example.
An application program (also known as a software application, or simply an app) is a computer program that performs a specific task other than one relating to the operation of the computer itself, typically to be used by end-users. Word processors, media players, and accounting software are examples of application programs.
Example :
- Microsoft Office suite (Word, Excel, PowerPoint, Outlook)
- Google Docs, Sheets, Slides, Gmail
- Adobe Photoshop, Illustrator, Premiere Pro
- Spotify, Apple Music, Netflix.
f. What is PWD command in unix.
The pwd command in Unix is used to print the full pathname of the current working directory. The current working directory is the directory that you are currently in. The pwd command is a shell builtin, which means that it is built into the shell and does not need to be called as an external program.
g. Write the purpose of DBMS.
The purpose of a database management system (DBMS) is to provide a way to store, organize, and manage data. DBMSs provide a number of features that make them ideal for managing large amounts of data, including:
h. Expand WWW and https.
WWW stands for World Wide Web
HTTPS stands for Hypertext Transfer Protocol Secure
Section - B
Answer any Three Questions.
a. Describe I and II Generation computers.
First generation computers
First generation computers were developed in the 1940s and 1950s. They were large, expensive, and unreliable. They used vacuum tubes for processing and magnetic drums for storage. Vacuum tubes were large, fragile, and generated a lot of heat. Magnetic drums were slow and had a limited capacity.
First generation computers were used for scientific and military applications. They were also used for some business applications, such as payroll and accounting.
Examples of first generation computers:
- ENIAC
- Colossus
- UNIVAC I
- IBM 701
Second generation computers :
Second generation computers were developed in the 1950s and 1960s. They used transistors instead of vacuum tubes. Transistors were smaller, more reliable, and produced less heat than vacuum tubes. Second generation computers also used magnetic core memory instead of magnetic drums. Magnetic core memory was faster and had a larger capacity than magnetic drums.
Second generation computers were smaller, faster, and more reliable than first generation computers. They were also more affordable, which made them more accessible to businesses and universities.
Second generation computers were used for a wide variety of applications, including scientific and military applications, business applications, and educational applications.
Examples of second generation computers:
- IBM 1401
- IBM 7090
- CDC 1604
- UNIVAC II

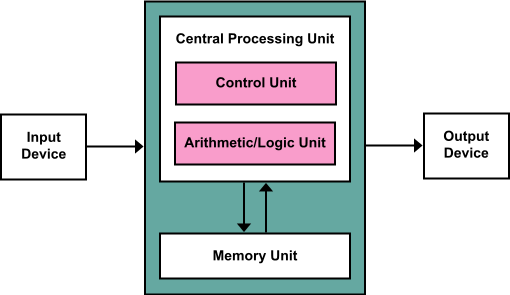
b. Write the function of CU and ALU.
The control unit (CU) and arithmetic logic unit (ALU) are two of the most important components of a central processing unit (CPU). The CU is responsible for fetching, decoding, and executing instructions. The ALU is responsible for performing arithmetic and logic operations.
Function of the CU :
- The CU is the brain of the CPU. It is responsible for controlling all of the other components of the CPU, including the ALU, memory, and input/output devices. The CU fetches instructions from memory, decodes them, and then executes them.
- To fetch an instruction, the CU sends a signal to memory to read the instruction at a specific address. Once the instruction has been read, the CU decodes it to determine what operation needs to be performed. The CU then sends signals to the ALU to perform the operation.
- The CU also monitors the status of the ALU and other components of the CPU. For example, if the ALU generates an error, the CU can stop the execution of the current instruction and take corrective action.
Function of the ALU :
- The ALU is the workhorse of the CPU. It is responsible for performing all of the arithmetic and logic operations that are required by the computer. The ALU can perform basic operations such as addition, subtraction, multiplication, and division. It can also perform more complex operations such as comparison, logical AND, and logical OR.
- The ALU receives operands from memory or from other registers. It then performs the specified operation on the operands and produces a result. The result is then stored in memory or in a register.
c. Explain any two Input devices with their neat diagram.
A keyboard is an input device that allows users to enter data into a computer. It consists of a set of keys that are arranged in a specific layout. The most common keyboard layout is the QWERTY layout.
The keys on the keyboard are:
- Numeric Keys: These keys are used to enter numeric data and move the cursor. It is typically made up of 17 keys.
- Keyboard Shortcuts: These keys include the letter keys (A-Z) and the number keys (09).
- Control Keys: The pointer and the screen are controlled by these keys. It comes with four directional arrow keys. Control keys include Home, End, Insert, Alternate(Alt), Delete, Control(Ctrl), and Escape.
- Special Keys: Enter, Shift, Caps Lock, NumLk, Tab, and Print Screen are some of the special function keys on the keyboard.
- Function Keys: The 12 keys from F1 to F12 are on the topmost row of the keyboard.

Mouse are also input devices that allow users to interact with a computer. They are typically handheld devices that have one or more buttons and a scroll wheel.
Characteristics of the mouse:
- A mouse is used to move the cursor on the screen in the desired direction.
- A mouse allows users to choose files, folders, or multiple files or text or, all at once.
- Hover over any object with the mouse pointer.
- A mouse can be used to open a file, folder, etc. You must first move your pointer to a file, folder, and then double-click on it to open or execute.

d. Explain CPU of Computer.
The Central Processing Unit (CPU), also known as the central processor or main processor, is the most important processor in a given computer. Its electronic circuitry executes instructions of a computer program, such as arithmetic, logic, controlling, and input/output (I/O) operations. This role contrasts with that of external components, such as main memory and I/O circuitry, and specialized coprocessors such as graphics processing units (GPUs).
The CPU is often called the “brain” of the computer because it is responsible for carrying out all the instructions that tell the computer what to do. It does this by fetching instructions from memory, decoding them, and then executing them. The CPU also performs all the calculations that are necessary to run programs, such as adding, subtracting, multiplying, and dividing numbers.
Answer any Three Questions.
a. What is non-positional numbering system? Give example.
A non-positional numbering system is a system in which the value of a digit does not depend on its position within the number. This is in contrast to a positional numbering system, such as the decimal system, in which the value of a digit does depend on its position.
An example of a non-positional numbering system is the Roman numeral system. In the Roman numeral system, the digit “I” always represents the value 1, regardless of its position in the number. For example, the number “II” represents the value 2, and the number “III” represents the value 3.
Another example of a non-positional numbering system is the Egyptian hieroglyphic numeral system. In the Egyptian hieroglyphic numeral system, there are different symbols for different powers of 10. For example, the symbol for 10 is a straight line, and the symbol for 100 is a bent line. The number “16” would be written as one bent line and six straight lines.
Non-positional numbering systems are often more difficult to use than positional numbering systems, but they can be more efficient for representing certain types of numbers. For example, the Roman numeral system is often used to represent dates, because it is more efficient to write “MMXXII” than “2022”.
Here are some other examples of non-positional numbering systems:
- Babylonian numerals
- Mayan numerals
- Chinese numerals
- Japanese numerals
b. Convert the following (i) 1AF(16)_________(2) (ii) 248(10)=________(16).
Converting each hexadecimal digit to its equivalent binary representation, we get:
1 = 0001
10 = 1010
15 = 1111
Combining the binary representations of the hexadecimal digits, we get the binary representation of the original number:
1AF = 0001 1010 1111
For the decimal number 248, the following is the division process:
248 / 16 = 15 R 8
15 / 16 = 0 R 15
The remainders are 8 and 15, so the hexadecimal representation of 248 is F8.
Therefore, 248(10) = F8(16).
c. Explain machine level and assebmly level language.
Machine language is the lowest-level programming language that a computer can understand. It is a series of binary instructions that the computer can directly execute. Machine language instructions are typically represented as a sequence of 0s and 1s.
Assembly language is a slightly higher-level programming language than machine language. It uses mnemonic codes to represent machine language instructions. Mnemonic codes are abbreviations for machine language instructions, and they are easier for humans to read and write than binary instructions.
Example :
10101100 00000011
Here are some examples of when machine language and assembly language might be used:
Machine language:
• Operating systems
• Device drivers
• Embedded systems
Assembly language:
• Video games
• Real-time systems
• Compilers and assemblers
• Device drivers
d. What is flowchart? list the symbols of flowchart.
A flowchart is a graphical representation of a process or algorithm. It is a type of diagram that uses symbols and arrows to show the steps involved in a process and the sequence in which those steps are performed.
Flowcharts are used in a variety of fields, including computer science, business, and engineering. They can be used to document existing processes, design new processes, or communicate processes to others.
Here are some of the most common flowchart symbols:
Terminator: This symbol represents the start or end of a flowchart.
Process: This symbol represents a step in a process.
Decision: This symbol represents a decision that needs to be made.
Connector: This symbol connects different parts of a flowchart.
Input/Output: This symbol represents input or output to or from the process.
Flowline: This symbol shows the direction of the flow of the process.

Answer any Three Questions.
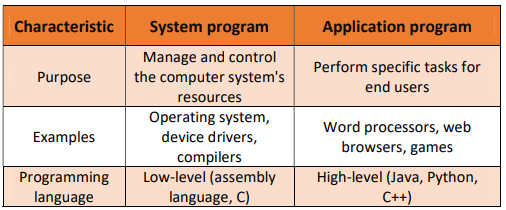
a. What are system program and application program.
System programs are programs that manage and control the computer system’s resources, such as the CPU, memory, and storage. They provide the foundation for application programs to run. System programs are typically written in low-level programming languages, such as assembly language or C.
Application programs are programs that are used by end users to perform specific tasks, such as word processing, web browsing, or playing games. They are typically written in high-level programming languages, such as Java, Python, or C++.
Here are some examples of system programs:
• Operating system
• Device drivers
• Compilers
• Assemblers
• Linkers
• Loader
• File system
• Network stack
Here are some examples of application programs:
• Word processors
• Web browsers
• Email clients
• Media players
• Games
• Productivity applications
• Business applications
• Educational applications
b. Discuss multi processing & time sharing Systems.
1.Multiprocessing is a computer architecture that uses multiple processors to execute multiple processes simultaneously. This can improve the overall performance of the system by distributing the workload across the different processors.
Main types:
1. Symmetric multiprocessing (SMP)
2. Asymmetric multiprocessing (AMP).
SMP systems have multiple processors that are equivalent and share the same memory. This makes it easy to distribute the workload evenly across the different processors.
AMP systems have multiple processors that are not equivalent and may not share the same memory. This makes it more difficult to distribute the workload evenly, but it can be used to create systems with a wider range of capabilities.
2.Time-sharing is a system that allows multiple users to share a single computer system simultaneously. This is done by dividing the CPU time into small slices and allocating each slice to a different user. The slices are so small that each user appears to have their own dedicated CPU.
Time-sharing systems are typically used on multiprocessor systems, but they can also be used on single-processor systems.
Here are some of the benefits of multiprocessing and time-sharing systems:
• Improved performance
• Increased throughput
• Improved reliability
• Better resource utilization
Examples of multiprocessing and time-sharing systems:
Multiprocessor systems:
• SMP servers
• Blade servers
• High-performance computing clusters
Time-sharing systems:
• Mainframe computers
• Minicomputers
• Multiuser workstations
c. Explain Unix Architecture.

The Unix architecture is a layered system that consists of four main layers:
Kernel: The kernel is the core of the Unix operating system. It is responsible for managing the hardware resources of the system, such as the CPU, memory, and storage. The kernel also provides basic services to other programs, such as file management, process management, and networking.
Shell: The shell is a user interface that allows users to interact with the Unix operating system. It provides a command-line interface where users can enter commands to perform various tasks. The shell also interprets commands and executes them by calling the appropriate kernel functions.
System utilities: The system utilities are a collection of programs that provide basic functionality to users. These programs include things like file management tools, text processing tools, and network utilities.
Application programs: Application programs are programs that are written to perform specific tasks, such as word processing, web browsing, or playing games. Application programs typically use the system utilities and the kernel to perform their tasks.
Hardware : Hardware in Unix OS refers to the physical components of a computer system, such as the CPU, memory, storage, and peripherals. The Unix operating system interacts with the hardware through the kernel, which is the core of the operating system.
d. Write the purpose of cat, CP, rm amd MV command with syntax and example.
The cat, cp, rm, and mv commands are some of the most commonly used commands in Unix and Linux systems. They are used to perform basic file operations, such as viewing, copying, moving, and deleting files.
1.cat
The cat command is used to view the contents of a file. It can also be used to combine the contents of multiple files into a single file.
Syntax:
cat [options] [file1] [file2] …
Options:
-n: Number each line of output.
-b: Number each non-blank line of output.
-E: Display non-printing characters as escape sequences.
-T: Display tabs as ^I.
Examples:
View the contents of the file “myfile.txt”
cat myfile.txt
Combine the contents of the files “myfile1.txt” and “myfile2.txt” into a single file called “combined.txt”
cat myfile1.txt myfile2.txt > combined.txt
2.cp
The cp command is used to copy files and directories.
Syntax:
cp [options] source destination
Options:
-r: Copy directories recursively.
-p: Preserve the permissions, ownership, and modification time of the source files.
-f: Force the copy to overwrite existing files without prompting.
Examples:
Copy the file “myfile.txt” to the directory “/tmp”
cp myfile.txt /tmp
Copy the directory “mydir” and all of its contents to the directory “/home/user”
cp -r mydir /home/user
Force the copy of the file “myfile.txt” to overwrite the existing file with the same name in the directory “/tmp”
cp -f myfile.txt /tmp
3.rm
The rm command is used to remove files and directories.
Syntax:
rm [options] files
Options:
-r: Remove directories recursively.
-f: Force the removal of files without prompting.
-i: Prompt for confirmation before removing files.
Examples:
# Remove the file “myfile.txt”
rm myfile.txt
# Remove the directory “mydir” and all of its contents
rm -r mydir
# Force the removal of the file “myfile.txt” without prompting
rm -f myfile.txt
4.mv
The mv command is used to move or rename files and directories.
Syntax:
mv [options] source destination
Options:
-f: Force the move to overwrite existing files without prompting.
-i: Prompt for confirmation before moving files.
Examples:
Move the file “myfile.txt” to the directory “/tmp”
mv myfile.txt /tmp
Rename the file “myfile.txt” to “newfile.txt”
mv myfile.txt newfile.txt
Force the move of the file “myfile.txt” to overwrite the existing file with the same name in the directory “/tmp”
mv -f myfile.txt /tmp The cat, cp, rm, and mv commands are essential tools for managing files and directories in Unix and Linux systems. They are easy to use and can be used to perform a variety of tasks.
Answer any Three Questions.
a. Describe the application of database.
Applications :
- Accounting and finance: Databases are used to store and manage financial data, such as customer and vendor information, sales and purchase data, and accounting transactions.
- E-commerce: Databases are used to store and manage product information, customer information, and order data for e-commerce websites.
- Human resources: Databases are used to store and manage employee information, such as contact information, job history, and performance reviews.
- Manufacturing: Databases are used to store and manage product information, production schedules, and inventory data.
- Healthcare: Databases are used to store and manage patient information, medical records, and insurance data.
- Education: Databases are used to store and manage student information, grades, and course schedules.
- Government: Databases are used to store and manage citizen information, tax data, and law enforcement data.
- Research: Databases are used to store and manage scientific data, experimental results, and bibliographic information.
Specific Applications :
- To store and manage website content
- To power social media platforms
- To track and analyze customer behavior
- To develop and train machine learning models
- To store and manage data for video games and other interactive applications
b. What is DBS? list the roles of DBA.
DBS stands for Database Administrator. A Database Administrator (DBA) is responsible for the management and maintenance of a database system.
This includes tasks such as:
- Database design
- Database installation and configuration
- Database performance monitoring and tuning
- Database security
- Database backup and recovery
- Database troubleshooting
The roles and responsibilities of a DBA:
- Database design: DBAs work with developers and other stakeholders to design databases that meet the needs of the organization. This includes defining the database schema, creating tables and views, and setting up relationships between tables.
- Database installation and configuration: DBAs install and configure database software and hardware. This includes setting up database users and permissions, configuring database parameters, and creating database backups.
- Database performance monitoring and tuning: DBAs monitor the performance of databases and make necessary adjustments to improve performance. This includes identifying performance bottlenecks, optimizing database queries, and adjusting database settings.
- Database security: DBAs implement and maintain security measures to protect databases from unauthorized access and attack. This includes creating user accounts and assigning permissions, implementing access control lists (ACLs), and encrypting sensitive data.
- Database backup and recovery: DBAs implement backup and recovery procedures to protect databases from data loss. This includes creating regular backups of databases and testing backup and recovery procedures on a regular basis.
- Database troubleshooting: DBAs troubleshoot database problems and resolve them as quickly as possible. This includes identifying the cause of database problems and implementing solutions to fix the problems.
c. List the Services of Internet.
The internet provides a wide range of services, including:
- Communication services: Email, instant messaging, video conferencing, social media, and other communication services allow users to connect and communicate with each other from anywhere in the world.
- Information retrieval services: Web search engines, online databases, and other information retrieval services allow users to find information on a wide range of topics.
- File transfer services: FTP (File Transfer Protocol) and other file transfer services allow users to transfer files between computers.
- World Wide Web services: The World Wide Web (WWW) is a system of interlinked hypertext documents that are accessed via the internet. The WWW provides access to a wide range of information and services, including websites, web applications, and web-based games.
- Web services: Web services are software components that can be accessed over the internet. Web services can be used to perform a wide range of tasks, such as sending emails, processing payments, and booking flights.
Basic Services :
- E-commerce: E-commerce services allow users to buy and sell goods and services online.
- Online banking: Online banking services allow users to manage their finances online.
- Online education: Online education services allow users to take courses and earn degrees online.
- Online entertainment: Online entertainment services allow users to watch movies, listen to music, and play games online.
- Online government services: Online government services allow users to access government services online, such as filing taxes and renewing passports.
d. What is Web Browser? List any four web browsers.
A web browser is a software application that allows users to access websites on the Internet. When a user requests a web page from a particular website, the browser retrieves its files from a web server and then displays the page on the user’s screen.
Here is a list of four web browsers:
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Safari
These browsers are all popular and widely used, and they offer a variety of features and functionality.
- Google Chrome: Chrome is a fast and secure web browser that is developed by Google. It is one of the most popular web browsers in the world.
- Mozilla Firefox: Firefox is a free and open-source web browser that is developed by the Mozilla Foundation. It is known for its privacy features and its support for extensions and add-ons.
- Microsoft Edge: Edge is a web browser that is developed by Microsoft. It is the default web browser in the Windows operating system.
- Safari: Safari is a web browser that is developed by Apple. It is the default web browser on macOS and iOS devices.
